Data from a cybersecurity firm’s user base for 2021 points to cybercriminals’ increasing sophistication at penetration and evasion.
Compiling threat data from its threat hunting, threat intelligence and threat services team, cybersecurity firm CrowdStrike has released its annual report of the threat landscape for 2021.
The firm’s threat hunters report directly identifying and helping to disrupt more than 65,000 potential intrusions (approximately one potential intrusion every eight minutes) in its user base. The “explosion in adversary activity” also included a 60% increase in attempted intrusions spanning all industry verticals and geographic regions studied.
Other findings include:
- Average breakout time—the time it takes for an intruder to begin moving laterally outside of the initial beachhead to other systems in the network has dropped to one hour 32 minutes, one third of the 2020 figures.
- Adversaries have moved beyond malware: Cybercriminals in the study were using increasingly sophisticated and stealthy techniques tailor-made to evade detections. Of all of the detections indexed by the firm in the past three months, 68% were malware-free.
- China, North Korea and Iran were the most active state-sponsored groups
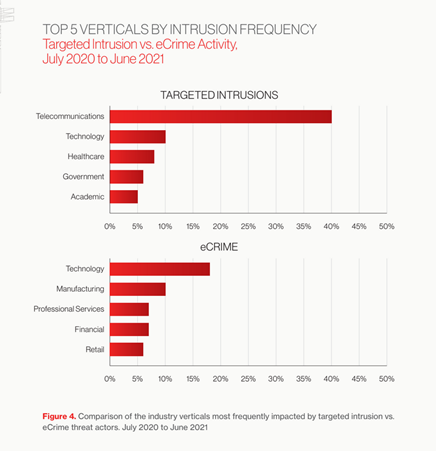
- A massive surge in interactive intrusion activity targeting the telecommunications industry: This activity spanned all major geographic regions studied and was tied to a diverse range of adversaries.
- WIZARD SPIDER was the most prolific cybercriminal in the user base. This threat group was seen in nearly double the number of attempted intrusions than any other cybercriminal group in the firm’s user base. WIZARD SPIDER is behind targeted operations using Ryuk and, more recently, Conti ransomware.
- 100% increase in instances of cryptojacking: This was viainteractive intrusions year-over-year, correlating with increases in cryptocurrency prices.
- Access Brokers had a banner year: This threat groupspecializes in breaching networks to sell access to others. They played a growing and important role for other threat actors to stage their attempted intrusions.
According to Param Singh, Vice President, Falcon OverWatch, CrowdStrike: “In order to thwart modern adversaries’ stealthy and unabashed tactics and techniques, it’s imperative that organizations incorporate both expert threat hunting and threat intelligence into their security stacks, layer machine-learning enabled endpoint detection and response (EDR) into their networks and have comprehensive visibility into endpoints to ultimately stop adversaries in their tracks.”

















