This is one of several trends noted in one DDoS mitigation firm’s Q3 user ecosystem data.
In analyzing its customer protection ecosystem between 1 July through September 30, 2022, a cybersecurity firm has reported a 21% increase in distributed denial-of-service attacks (DDoS attacks) quarter-on-quarter, with a special focus on vulnerabilities in the Connectionless Lightweight Directory Access Protocol (CLDAP).
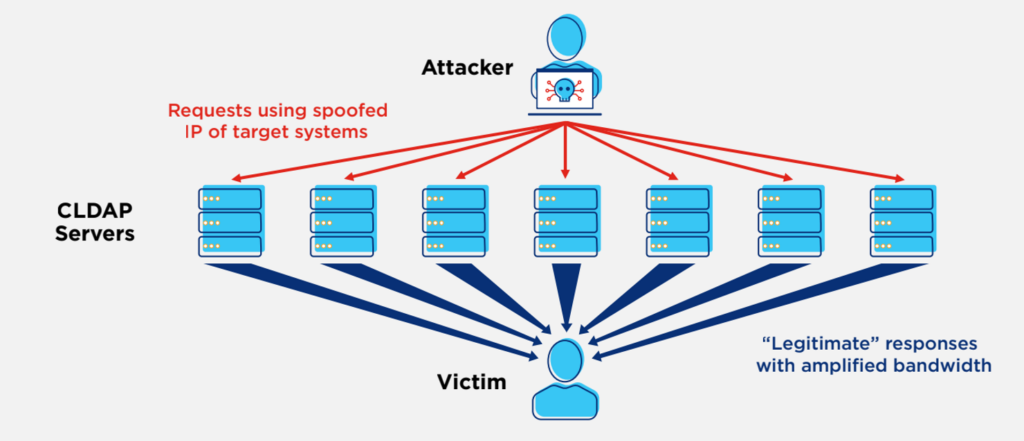
If a CLDAP has been misconfigured to be exposed to the internet, the service would be vulnerable to cyberattacks, allowing cybercriminals to launch reflective DDoS attacks with a bandwidth amplification factor of up to 70 times of the original request.
Highlights of the Q3 DDoS report also include the following:
- A total of 5,547 DDoS attacks, at 63 attacks per day, were mitigated — an increase of 21% over Q2. The average attack size in the ecosystem was 1.4Gbps, (18% increase from Q2). The average packet rate-based attack scrubbed was 434 Kpps, up 12% from the previous quarter.
- 83% of DDoS attack durations were under 30min, up 15% from the previous quarter.
- 169 seconds was the average DDoS attack period in Q3, while the longest recorded was 6 days.
- Multi-vector attacks were on the rise, accounting for 40% of attacks. These are layered DDoS attacks where cybercriminals use more than one method to attempt to disrupt an organization.
- The largest attacks in the ecosystem targeted the Telecoms, Gaming and Software & Technology industries.
- Attackers were exploiting vulnerabilities in essential services to amplify attacks up to 70 times in size
- ‘Hit-and-run’ attacks — where threat actors deploy smaller and shorter attack campaigns to evaluate targeted organizations’ defenses — were continuing in trend
- Attacks on the ecosystem users during public holidays were noted as ideal attack windows for adversaries due to the potential for understaffing of IT and security activities
The report by Lumen also summarizes some DDoS myths: that small or short DDoS attacks can be ignored; that DDoS protection alone (without additional threat intelligence) is enough; and organizations not in the targeted industries are safe.