MS Sway, Sharepoint and OneNote have been used to host fake phishing pages targeting the personal data of key executives.
Aseries of sophisticated successful phishing attacks against the management and executives of more than 150 companies around the world has been brought to light recently.
The campaign, dubbed PerSwaysion due to the extensive abuse of Microsoft Sway, a content design application. PerSwaysion had been active since at least mid-2019 and was attributed to Vietnamese speaking developers and Nigerian operators. Сybercriminals behind the PerSwaysion campaign had gained access to many confidential corporate MS Office365 emails of mainly financial service companies, law firms, and real estate groups.
By leveraging compromised accounts’ email data to select further targets that hold important roles in their companies and share business relations with the victims, the PerSwaysion campaign has proliferated with alarming rates.
The researchers who identified PerSwaysion, Group-IB, is continuing to work with the relevant parties in local countries to inform the affected companies of the breach.
Not coercion but PerSwaysion
One of the defining signatures of PerSwaysion is that it spreads like wildfire jumping from one victim to another while no malware is present on a user device during the attack. A new round of phishing attempts leveraging a current victim’s account usually takes less than 24 hours.
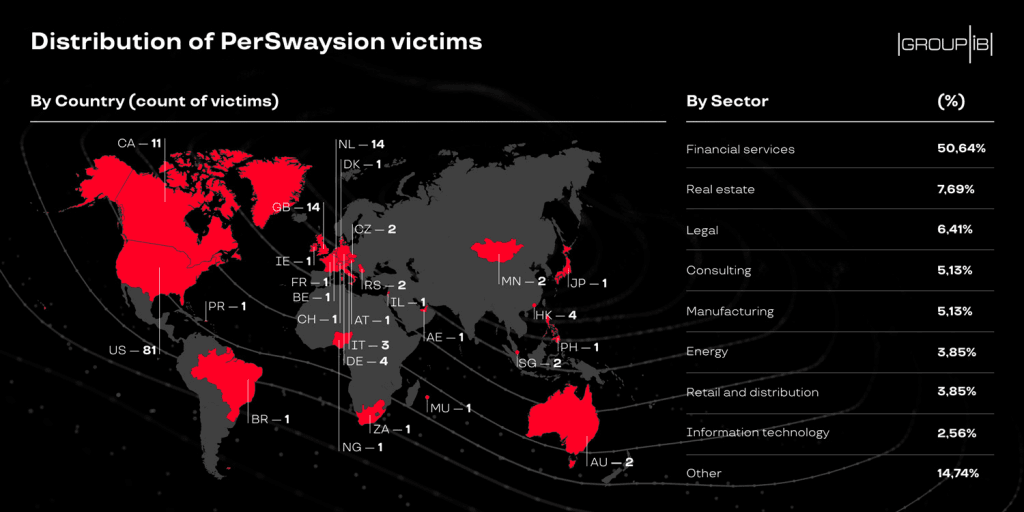
The campaign has so far resulted in a compromise of 156 high-ranking officers in global and regional financial hubs such as the US, Canada, Germany, the UK, Netherlands, Hong Kong, Singapore, and other locations.
The highly-targeted phishing campaign primarily focuses on financial services companies (~50%), law firms, and real estate companies to conduct further supply-chain attack against their clients and business contacts. Group-IB has set up a website, where everyone can check if their email has been compromised by PerSwaysion.
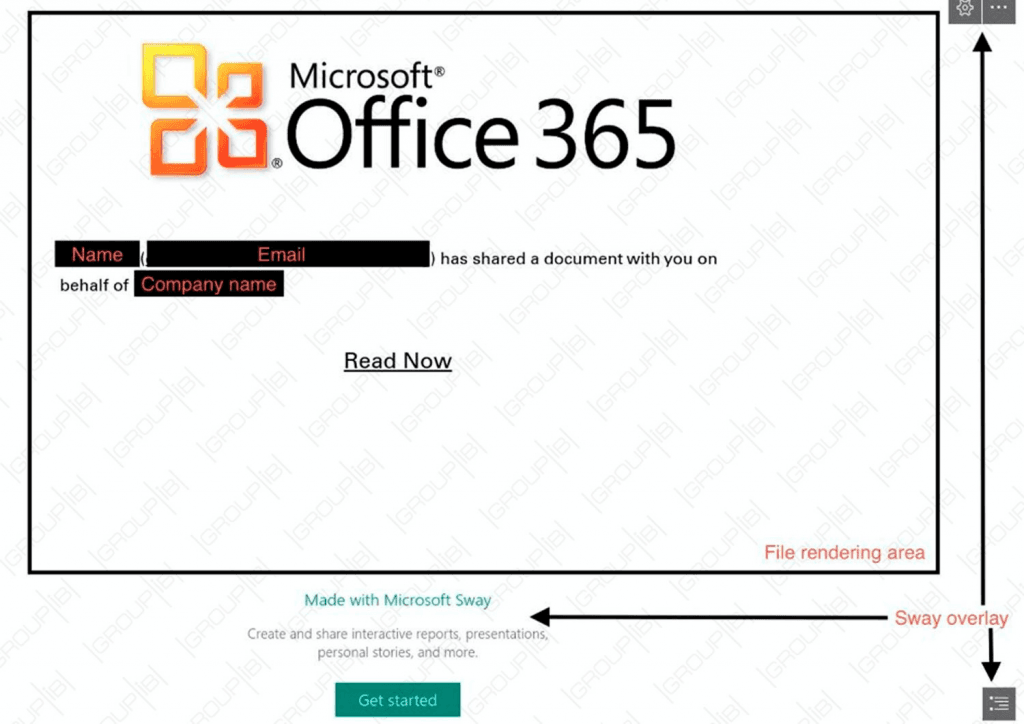
The three-phase attack first uses social-engineering methods to persuade high-level executives to opena non-malicious PDF email attachment coming from an authentic address in their contact list.
The PDF attachment is a well-crafted fake notification of Office 365 file sharing. The attackers pick legitimate cloud-based content sharing services, such as Microsoft Sway, Microsoft SharePoint, and OneNote to avoid traffic detection. In this case, upon clicking “Read Now”, the victim is taken to a file hosted on MS Sway. The page resembles an authentic Microsoft Office 365 file sharing page. However, this is a specially crafted presentation page which abuses Sway’s default borderless view.
From this page the targeted individual is redirected to the final destination, the actual phishing site disguised as a 2017 version of the Microsoft Single Sign-On page. Here the victim is assigned a unique serial number by the phishing kit, which serves as a rudimentary fingerprinting technique. Any repeated request to the exact same URL will be rejected. It stops any automated threat detection efforts to URLs visited by the targets. When the high-level employee submits corporate Office 365 credentials, the information is sent to a separate data server with an extra email address which is hidden on the page. This extra email is used as a real-time notification method to make sure attackers react on freshly harvested credentials.
Gone in 24 Hours
PerSwaysion threat actors conduct follow-up operations with newly-collected account credentials of high-ranking officers very quickly. Group-IB researchers revealed that the attackers take three main steps to push a new round of phishing against users whom the victims had recent correspondence with, which on average takes less than 24 hours.
After the credentials are sent to their masterminds the PerSwaysion operators log into the compromised email accounts. They dump email data via API and establish the owner’s high-level business connections. Finally, they generate new phishing PDF files with the current victim’s full name, email address, company legal name. These PDF files are sent to a selection of new people who tend to be outside of the victim’s organization and hold significant positions. The PerSwaysion operators typically delete impersonating emails from the outbox to avoid suspicion.
Said Feixiang He, senior Threat Intelligence analyst at Group-IB: “PerSwaysion threat actors have not demonstrated clear preferences of financial profit-generating models yet. The attackers hold covert access to many corporate email accounts and large piles of sensitive business email data of high-level management. Hence, it opens up a wide range of possibilities. The account access could be sold in bulk to other cybercriminals to conduct traditional monetary scams. Sensitive business data extracted from emails, such as non-public financial records, secret trading strategies, and client lists, could be sold to the highest bidder in the underground markets.”
Who are “The PerSwayders”?
The PerSwaysion campaign is a series of Malware-as-a-Service-based operations. Analysis of the campaign’s phishing kit reveals that it was primarily developed by highly specialized Vietnamese-speaking threat actors.
The user input validation module (VeeValidate) used in code only includes Vietnamese locale while 48 languages are supported. Further research has determined that the developer groups do not run phishing campaigns themselves. Instead, the developers likely sell their phishing kit and PDF generator to various cybercriminals for direct profit.
Group-IB Threat Intelligence has so far tracked down several loosely connected sub-groups of threat actors carrying out phishing attacks independently. These actors control a total of 27 email addresses used for stolen email account credentials collection and notifications. These emails were embedded in variants of PerSwaysion phishing kits. Some of these emails were used to register LinkedIn accounts for gathering potential victim profiles. Such data helps PerSwaysion attackers to pick people holding significant corporate positions.
Further investigations show one of PerSwaysion earliest operation teams is a group of threat actors who operate in Nigeria and South Africa. The group is allegedly led by a Nigerian who goes by the nickname Sam. This group has been conducting various activities ranging from online shopping scams to phishing attacks since 2017. The vast differences in geo-locations and cultures between phishing kit developers and campaign operators indicate great specialization among cybercriminals.
Said Feixiang He: “The PerSwaysion campaign is an example of highly-specialized phishing threat actors working together to conduct effective attacks on high ranking officers on a large scale. They adopt multiple tactics and techniques to avoid traffic detection and automated threat intelligence gathering, such as the use of file-sharing services and web application hosting from reputable vendors. The campaign pursues non-trivial counterintelligence methods, for example, randomizing malicious JS file names and fingerprinting victims’ browsers and rejecting repeated visits. Such measures taken by cybercriminals seeking to garner sensitive corporate information require a non-standard approach to their detection and response.”
According to Group-IB, cloud-based corporate services such as MS Sway introduce new challenges to traditional cyber risk management frameworks. Proper cloud migration plans should consider provisions for early prevention, anomaly detection, and incident response. When adopting cloud-based corporate services, it is crucial to enforce 2FA authentication to mitigate risks of login credential theft. Furthermore, when planning cloud-based service architectures, corporate system administrators need to evaluate various logging options offered by could service providers and integrate activity log data into existing risk detection flows.

















