The status deems the group as financially-motivated and clues point to them originating from the Commonwealth of Independent States.
A threat cluster that has been targeting the financial sector since 2017 has been formally named FIN11, which stands for financially-motivated threat group 11.
According to Mandiant Threat Intelligence, FIN11 is reminiscent of another well-known group called APT1—they are not notable for their sophistication but for their sheer volume of activity. In the case of FIN11’s phishing operations, significant gaps exist, but when up to five high-volume campaigns are conducted per week, they add up to a sizable threat.
While many financially-motivated threat groups are short lived, FIN11 has been conducting these widespread phishing campaigns since at least 2016. From 2017 through 2018, the threat group primarily targeted organizations in the financial, retail, and hospitality sectors. However, in 2019 FIN11’s targeting expanded to include a diverse set of sectors and geographic regions. At this point, it would be difficult to name a client that FIN11 has not targeted.
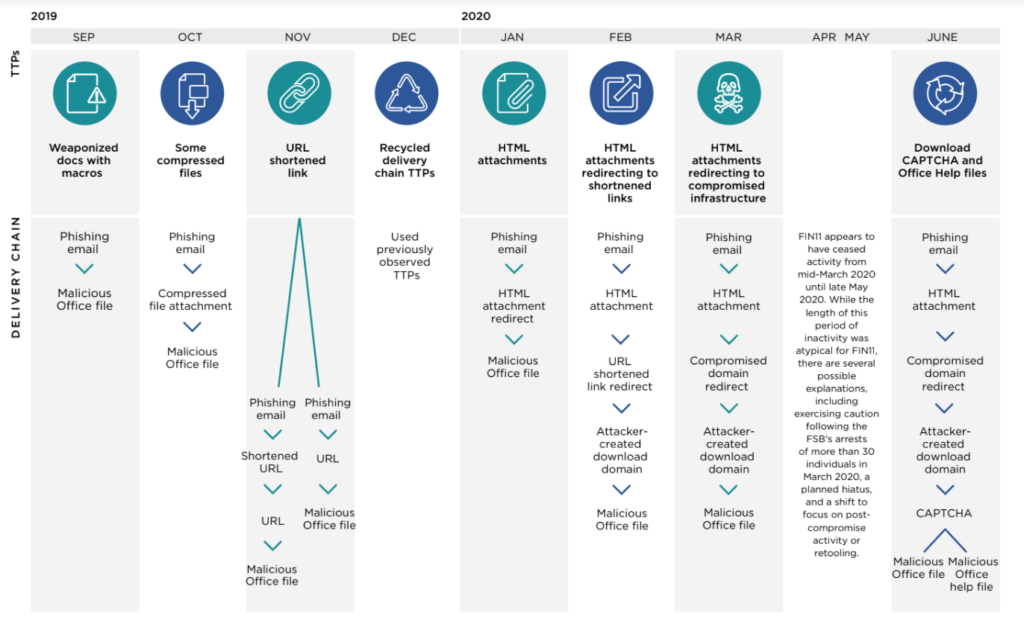
Mandiant has also responded to numerous FIN11 intrusions, but only in a few instances have the researchers observed the group successfully monetize access. This could suggest that the actors cast a wide net during their phishing operations, then choose which victims to further exploit based on characteristics such as sector, geolocation or perceived security posture.
Blackmail and ransomware
Recently, FIN11 has deployed CLOP ransomware and threatened to publish exfiltrated data to pressure victims into paying ransom demands. The group’s shifting monetization methods—from point-of-sale (POS) malware in 2018, to ransomware in 2019, and hybrid extortion in 2020—is part of a larger trend in which criminal actors have increasingly focused on post-compromise ransomware deployment and data theft extortion.
Notably, FIN11 includes a subset of the activity that security researchers call TA505, but Mandiant does not attribute TA505’s early operations to threat group and caution against using the names interchangeably. Attribution of both historic TA505 activity and more recent FIN11 activity is complicated by the actors’ use of criminal service providers.
Like most financially-motivated actors, FIN11 does not operate in a vacuum, and the group has used services that provide anonymous domain registration, bulletproof hosting, code signing certificates, and private or semi-private malware. Outsourcing work to these criminal service providers likely enables FIN11 to increase the scale and sophistication of their operations.

















