Here are two threats to take note of at year’s end as we enter another year full of cyberattack ingenuity.
As we reach the end of 2023, two cyber threats to watch out for are: fake browser updates and the TA422 advanced persistent threat.
In the first instance, Proofpoint has been tracking at least four distinct threat clusters that use fake browser updates to distribute malware.
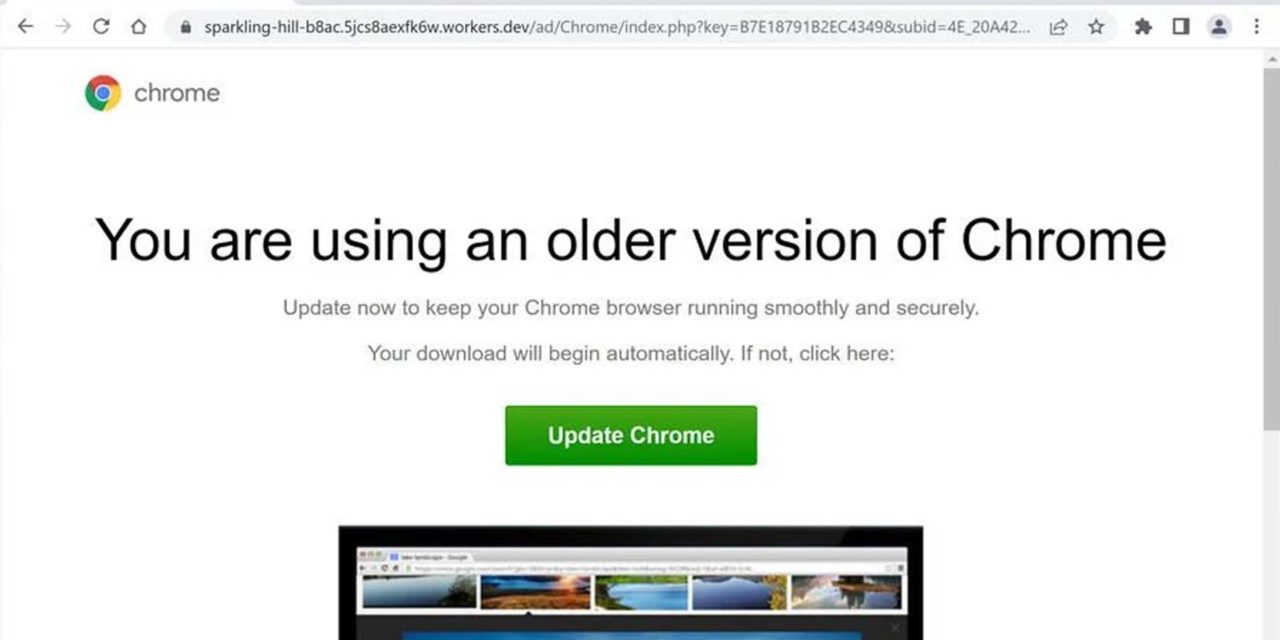
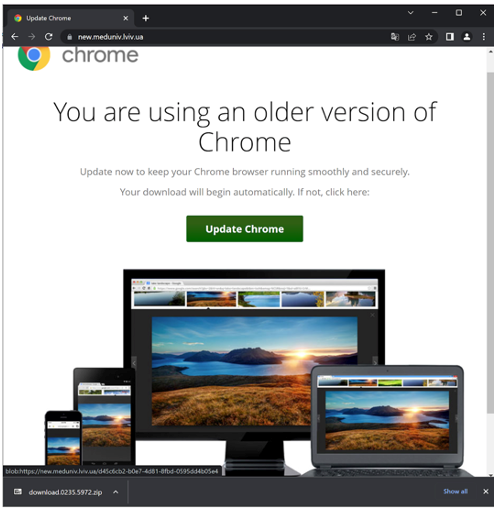
Fake browser updates refer to compromised websites that display what appears to be a notification from the browser developer such as Chrome, Firefox, or Edge, informing them that their browser software needs to be updated. When users click on the link, they do not download a legitimate browser update but rather, harmful malware.
Fake browser updates abuse end user trust with compromised websites and a lure customized to the victims’ browser, to legitimize the update.
Some characteristics of this threat:
- Threat actors do not send emails to share the compromised websites. The threat is only in the browser, and it can be initiated through a legitimate and expected email, social media site, search engine query, or even just navigating to a compromised site.
- Different campaigns push different payloads in their campaigns.
- Threat group TA569 delivers SocGholish malware — delivered via injected JavaScript on compromised websites. According to Proofpoint, it remains one of the most elusive malware families to date.
- A copycat campaign known as RogueRaticate or FakeSG. The fake update payload for these campaigns has always involved an HTML Application (.hta) file that is either zipped or downloaded via a shortcut (.url) file that points to the .lnk. The .hta file typically loads a malicious NetSupport remote access tool payload onto the host.
- The ZPHP/SmartApeSG campaign of Aug 2023 payload contains a JavaScript file that will load a malicious NetSupport remote access tool onto the host. Proofpoint researchers have also seen an executable that loads Lumma Stealer.
- Finally, ClearFake is a campaign that attempts to deliver a payload of either a malicious executable (sometimes zipped up), or .msi and .msix packages that install a variety of stealers including Lumma, Redline, and Raccoon v2.
- Specific indicators of compromise (IOCs) associated with the identified activities change regularly, as the threat actors are routinely moving their infrastructure and changing details in their payloads. The infosec. exchange account @monitorsg is a useful public resource for following along with recent details on payloads and infrastructure changes. The Emerging Threats Ruleset has domain rules available for most of the current threats and is regularly updating and publishing new rules to block all fake browser update campaigns.
Second threat: Dedicated Exploitation Loop
TA422 is a Russian advanced persistent threat (APT) that has readily used patched vulnerabilities to target organizations in Europe and North America, targeting organizations in the aerospace, education, finance, manufacturing, and technology sectors and governments to gain access to user credentials or initiate follow-on activity.
Some emails have even spoofed geopolitical entities, using the BRICS Summit and a European Parliament meeting as subject lures to entice targets to open the emails.
Proofpoint has observed over 10,000 repeated attempts exploiting a Microsoft Outlook elevation-of-privilege vulnerability, with the same accounts targeted daily this summer. TA422 campaigns have also been known to leverage a WinRAR remote execution vulnerability, CVE-2023-38831.