At the same time, email threats in Singapore saw a 30% increase for 1H 2019, compared to 1H 2018.
Trend Micro Incorporated just published its roundup report for the first half of 2019, which revealed a surge in fileless attacks that took advantage of a machine’s built-in tools and applications for attacks, leaving no identifiable signature behind. Detections of this threat alone were up 265% compared to the first half of 2018.
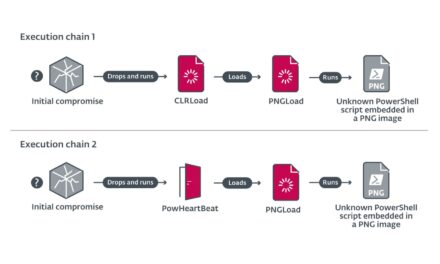
Fileless threats employed a variety of techniques as part of its infection routine. These can come from malicious macro codes in the form of JavaScript or VisualBasic (VBA) scripts embedded within Office documents, PDFs, archives, or seemingly benign files.
The report also revealed that email is still the most used threat vector deployed to infiltrate a corporate network and target unsuspecting employees. Email threats in Singapore saw a 30% increase for the first half of 2019, compared to the first half of 2018. This trend was possibly driven by cybercriminals moving to and favoring cloud-based or mobile platforms, such as Office 365, as avenues for scamming users and enterprises.
On a global level, business email compromise (BEC) remained a major threat, with detections jumping 52% compared to the past six months. The CEO remained the most spoofed position in BEC scams, as emails from CEOs tended to elicit a sense of urgency and inspire prompt action from the recipients. Employees targeted typically were those who were authorized to conduct wire transfers.
“Email remained a top threat vector in Singapore – we saw intentional, targeted, and crafty attacks that stealthily take advantage of people, processes, and technology. To navigate this evolution, businesses need a technology partner to build a secure foundation in cybersecurity, which is essential to driving Singapore’s Smart Nation agenda,” said Nilesh Jain, vice president of Southeast Asia and India, Trend Micro.
“The future of email security will also contend with threats that arise from the integration of workplace collaboration tools, such as Slack or Dropbox, with email platforms. As a rule of thumb, organizations should ensure that IT personnel are briefed and educated about the security repercussions, and put in sufficient security at the email gateway and for internal emails that don’t cross the gateway.”
The findings in 2019 so far confirmed many of the predictions Trend Micro made last year. Namely, attackers are working smarter to target businesses and environments that will produce the greatest return on investment.
Further 1H 2019 global threats trends at-a-glance:
- In terms of file-based threat components, cryptomining malware remained the most detected threat in the first half of 2019, with attackers increasingly deploying these threats on servers and in cloud environments. Substantiating another prediction, the number of routers involved in possible inbound attacks jumped 64% compared to the first half of 2018, with more Mirai variants searching for exposed devices.
- Digital extortion schemes soared by 319% from the second half of 2018, which aligns with previous projections.
- Ransomware-related files, emails, and URLs grew 77% over the same period.
- Exploit kits have also made a comeback, with a 136% increase compared to the same period in 2018.
In total, Trend Micro blocked more than 26.8 billion threats in the first half of 2019, over 6 billion more than the same period last year. Of note, 91% of these threats entered the corporate network via email.
Mitigating these advanced threats requires smart defense-in-depth that can correlate data from across gateways, networks, servers and endpoints to best identify and stop attacks.