Armed with features to evade detection and analysis, the Trojan has also incorporated social engineering weapons.
In the first seven months of 2021, the number of users attacked with QakBot, a powerful banking Trojan, grew by 65% (17,316 users) within a cybersecurity firm’s user ecosystem in comparison to the same period last year.
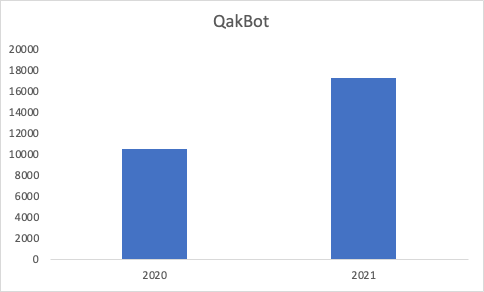
Banking trojans allow cybercriminals to steal money from victims’ online banking accounts and e-wallets. Although QakBot was identified as early as 2007, its developer only recently invested more into development, turning it into one of the most powerful and dangerous of its kind.
In addition to functions that are standard for banking trojans, such as keylogging, cookie-stealing, passwords and login grabbing, recent versions of QakBot have included functionalities and techniques allowing it to detect if it is running in a virtual environment. If so, it can stop suspicious activity or stop functioning completely. In addition, QakBot tries to protect itself from being analyzed and debugged by experts and automated tools.
Finally, recent versions of QakBot can steal emails from the attacked machine, for use in various social engineering campaigns against users in the victim’s email contact list.
According to one of the firm’s malware analysts Haim Zigel: “This malware continuously receives updates and the threat actors behind it keep adding new capabilities and updating its modules in order to maximize the revenue impact, along with stealing details and information. Previously, QakBot was being actively spread via the Emotet botnet. This botnet was taken down at the beginning of the year, but judging by the (recent rise in incidents), QakBot actors have found a new way of propagating this malicious software.”
Readers can minimize exposure to QakBot through the usual cyber hygiene best practices.

















