People who inadvertently installed a malware app may feel relieved that they had not launched it yet when informed, but …
Ordinary people may think that a malware app found installed on a smartphone is not a threat unless it is launched. However, in January 2021, cyber researchers uncovered a malware app that was also a trojan, due to the granting of access to the device’s call handling functions.
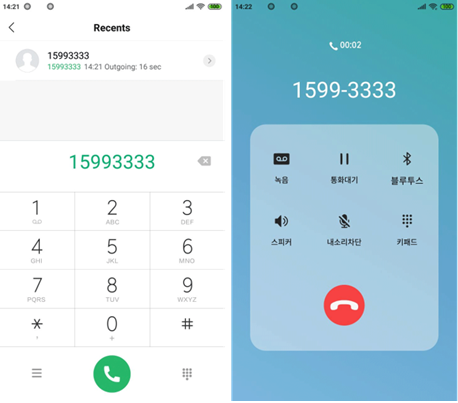
Then, even when the user does not launch the main app, trojan functions can lurk in the background, monitoring the phone’s activities: as soon as a user tries to call a bank to verify information, the trojan can intercept the call, present a fake screen call (see screenshot on this page) to make the user think that the call went through, and from there, allow impersonators at the other end of the line ‘authenticate’ whatever the user is checking.
As this ruse was launched in South Korea, cybercriminals failed to consider that some of their potential victims may use different interface languages, for example, English instead of Korean. As the fake call screen is in Korean, victims in other countries are more likely to smell a rat.
Intercepting calls convincingly
The trojanized malware, known as Fakecalls, is disguised as an ‘authentic’ banking app that expects users to grant a variety of permissions such as access to the smartphone’s contact list, microphone, camera, geolocation and call handling functions.
These permissions allow the trojan part of the app to drop incoming calls and delete them from the device’s history when a real bank is trying to reach its client.
The trojan is not only able to control incoming calls but it can also intercept outgoing calls and trick the user into thinking that the call went through as usual, even though the phone shows a mock call screen that contains the right call information. This is all fine in South Korea, but the ruse falls through in other countries or situations where any aspect of a Korean interface is not expected on a smartphone.
In fact, from time to time, the trojan inserts small audio snippets in Korean, such as “Hello. Thank you for calling our bank. Our call center is currently receiving an unusually large volume of calls. A consultant will speak with you as soon as possible.” Where applicable, this routine gain the trust of victims by making them believe that the call is real. Furthermore, Fakecalls completely mimics the mobile apps of well-known South Korean banks via the use of actual bank logos and support information as displayed on the main page of official bank websites.
In some scenarios, Fakecalls plays prerecorded audio (in Korean of course) that imitates a standard greeting from the bank and mimics a standard conversation using an automated voicemail.
The main objective of such fakery is to coax as much vulnerable information, including bank account details, from victims as possible.
Learning point: stay vigilant
According to Igor Golovin, Security Researcher, Kaspersky, which discovered the ruse in January 2021, banking clients are constantly told to be wary of calls from scammers. However, when they are directly trying to reach bank customer support themselves, they do not expect any danger.
“The cybercriminals that created Fakecalls have combined two dangerous technologies: banking trojans and social engineering, so their victims are more likely to lose money and personal data. Before downloading a new app, take into consideration what permissions it asks for. If it’s trying to get suspiciously excessive access to device controls, including call handling access, then it is most likely that the app is a banking trojan,” Golovin said.