The ransomware gang used stolen source code to disguise malware files as trustworthy to the operating system of targeted systems.
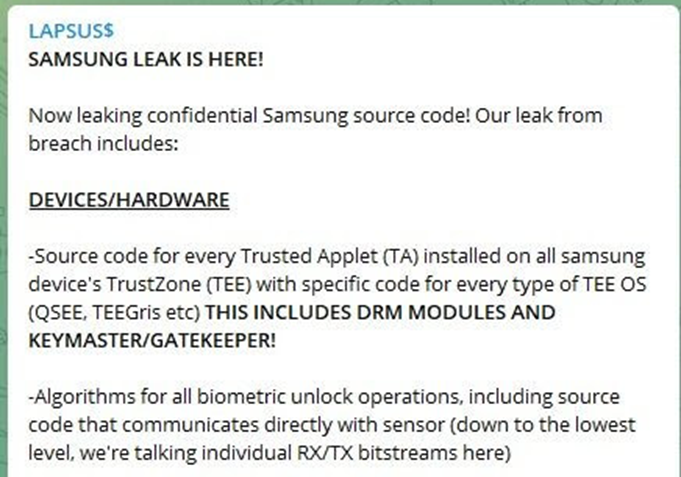
Samsung has announced that its internal data for Galaxy-branded smart devices had been hacked. Some 190GB of confidential source code for security firmware features such as Knox, biometric authentication; bootloaders security; hardware cryptography; binary encryption; access control; and even sensitive data from its chip supplied Qualcomm were released to the public.
Threat group Lapsus$ has taken responsibility for the breach, just as it had when it successfully hacked in to NVidia and leaked the employee credentials in a bid to force the firm to remove its cryptocurrency mining limiter ‘LHR’ from its high-end graphics processing cards.
Although no customer data is said to have been leaked, the public will wonder what the likely impact of hackers gaining possession and control over such proprietary features that protect hundreds of millions of Galaxy-branded smart devices.
Official responses
In their official public response, NVidia announced: “We have no evidence of ransomware being deployed on the NVIDIA environment or that this is related to the Russia-Ukraine conflict. However, we are aware that the threat actor took employee passwords and some NVIDIA proprietary information from our systems and has begun leaking it online.”
Samsung officially responded and confirmed the breach on 7 March 2022: “There was a security breach relating to certain internal company data. According to our initial analysis, the breach involves some source code relating to the operation of Galaxy devices, but does not include the personal information of our consumers or employees. Currently, we do not anticipate any impact to our business or customers.”
The threat group’s name Lapsus refers to “an involuntary mistake made while writing or speaking.” The threat group is thought to be based in Brazil. They gained infamy through notable attacks on the Brazilian health ministry, as well as firms such as Claro, Embratel, Impresa, Localiza and NET.
How they pulled it off
Lapsus$ attackers first managed to steal relevant code-signing certificates from the victimized firms that are routinely used to clear executables and software drivers as safe to execute on an operating system.
In the case of NVidia, two code signing certificates were compromised and then used to mark malware as ‘safe’ to targeted Windows machines in the network.
Although the stolen certificates had expired, hackers can still use them to make malicious software appear ‘certified safe’. The Windows operating system can then be fooled into executing the malicious code, thereby having other security measures bypassed.
Immediate steps to stay protected
According to Check Point Research (CPR), as far as the Samsung/NVidia incidents are concerned, organizations should be mainly on high alert about malware penetration into their corporate network via stolen certificates.
Unfortunately, some security solutions in the market still expose organizations to this supply chain threat, as they seem to automatically revoke the stolen certificates, most probably since they consider the vendor that produced the certificate as trusted by default.
To keep the entire IT infrastructure safe, CPR recommend organizations to update protection against stolen certificates in their network security gateways and endpoint device security solutions. Updates should be downloaded from formal vendor websites and rolled out to the entire workforce.
Countering such Lapsus attacks is complicated if Windows Defender Application Control policies are configured to ban drivers and executables involved in attacks. However, the safest solution is to rely on antimalware solutions that are regularly updated with threat intelligence information against stolen certificates and related threats.

















