Poor cyber-hygiene among SMEs are the predominant cause of the malspam onslaught.
This week, Unit 42, the threat intelligence arm of Palo Alto Networks, released a report detailing the recent movements of a malware called Emotet, that infects computer systems globally through its mass campaigns of spam email that delivers malware.
Emotet was initially designed to steal financial data, but it has since evolved into a malware loader with modular functionalities. This means that Emotet operators are now able to install additional malware onto infected machines and even offer their botnet as “Malware-as-a-Service” to other cyber-criminal gangs.
Key highlights from the report are:
- A large number of vulnerable servers belonging to SMEs across the APAC region were being exploited by Emotet actors to distribute Emotet variants. It is important to note that this exploitation is possible primarily due to poor cybersecurity hygiene on the part of these SMEs, such as failing to update and patch their web servers regularly.
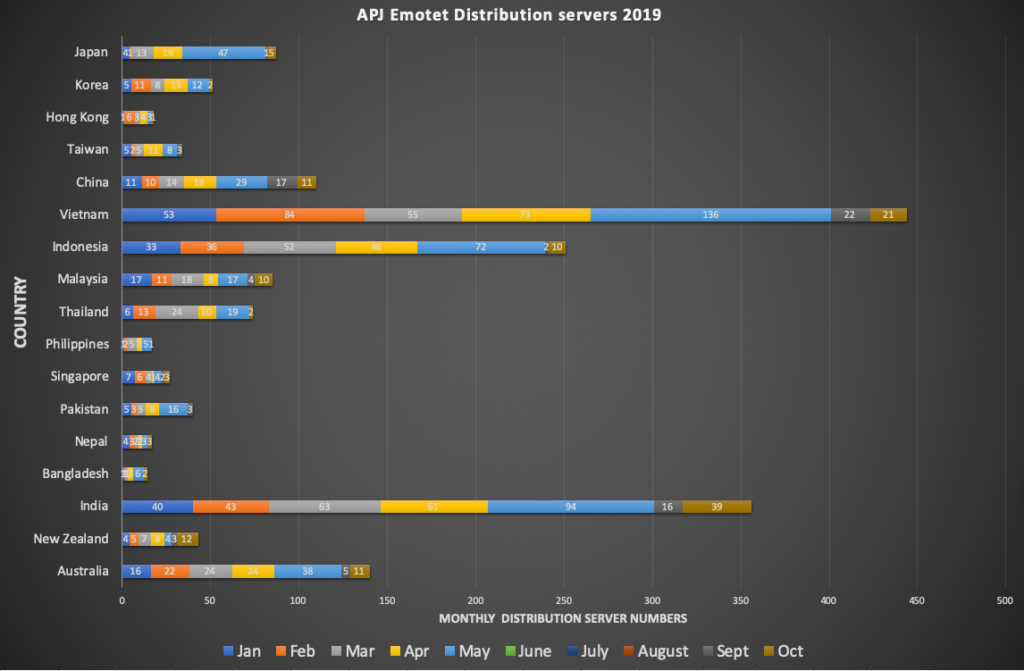
- Vietnam is the top affected country in the region, followed by India and Indonesia (see data below).
- The majority of these compromised domains are running on the WordPress blogging software.
A quick search for WordPress vulnerabilities on vulnerability tracker sites, like “CVE Details”, shows the high number of vulnerabilities that have been disclosed for WordPress. A similar search on “Exploit-DB” also shows the high number of exploits being published every month in the public domain, allowing anyone to reuse the exploits published.
While the understanding of Emotet actors exploiting vulnerable WordPress sites is not new to the security community, it is important to stress and highlight this again to raise the awareness for organizations to patch their web applications as soon as possible and deter threat actors like the Emotet gang to take advantage of the vulnerabilities and avoid a more devastating impact.
While Emotet has already been active for a number of years, their ongoing campaign numbers, modular platform, disruptive capability, related incidents and the associated recovery costs for organizations show that this is one of the most significant cyber threats of the current era.
The report’s emphasis on the distribution servers across the APAC region is to play up visibility on regional, in-country numbers and also to streamline remediation efforts and raise awareness on how cybercriminals are taking advantage of vulnerable SME’s.
Unit 42 reiterates that it is imperative for SME’s to improve their cyber-hygiene process of patching their respective web-servers and applications.

















