Using a photograph and a specific type of USB camera, hackers can bypass Windows Hello facial authentication.
Recently, Microsoft disclosed a vulnerability (CVE-2021-34466) in its Windows Hello Security feature, where potentially any authentication system that allows a pluggable third-party USB camera to act as biometric sensor could be susceptible to this attack without proper mitigation.
The vulnerability has been assigned a CVE (base score 5.7) and a security update and mitigation advice have been issued.
According to Microsoft, Windows Hello is used by 85% of Windows 10 users. An advanced version, Windows Hello for Business, takes the offered authentication features to an enterprise-grade suitable solution. Windows Hello for Business uses a PIN code backed by an asymmetric pair of public and private keys or certificate-based authentication.
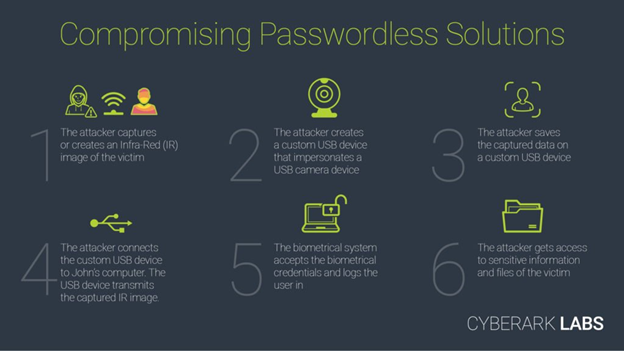
Research by CyberArk Labs, which disclosed the vulnerability, had uncovered a significant vulnerability in Windows Hello for Business that allows an attacker to bypass facial recognition authentication on a target’s device.
The research team had found a way to manipulate the security aspects behind the facial-recognition mechanism used by Windows Hello—via a custom-made USB camera and a photo of the target. While the researchers’ focus was Windows Hello, the proof of concept has implications for any authentication system that allows a pluggable third-party USB camera to act as biometric sensor.
As the research has shown, this type of attack is highly relevant for targeted espionage, where the target is known and physical access is needed on a device (this would be a highly effective attack on a researcher, scientist, journalist, activist or someone else with IP on their device).
According to CyberArk security researcher Omer Tsarfati, their proof of concept on how to bypass facial recognition for authentication could have a similar impact on targeted espionage campaigns around the world. “Based on our preliminary testing of the mitigation, using Enhanced Sign-in Security with compatible hardware limits the attack surface but is dependent on users having specific cameras. Inherent to system design, implicit trust of input from peripheral devices remains. To mitigate this inherent trust issue more comprehensively, the host should validate the integrity of the biometric authentication device before trusting it. We are continuing our investigation.”

















