Hackers coordinated a social engineering attack and gained insider access to hundreds of major high-profile social media accounts.
On 15 July 2020 (US time zones), it became known that Twitter accounts of major US tech figures, companies, politicians and celebrities have been hijacked in what turned out to be one of the biggest attacks in the history of the social network.
Hacked accounts included those of Barack Obama, Joe Biden, Bill Gates, Kim Kardashian West, Warren Buffett, Jeff Bezos, Elon Musk, Mike Bloomberg, and Apple.
According to Twitter Support, this was a coordinated social engineering attack by people who successfully targeted some of their employees with access to internal systems and tools.
Group-IB’s threat researchers report that more than 100 accounts have been hijacked by the attackers.
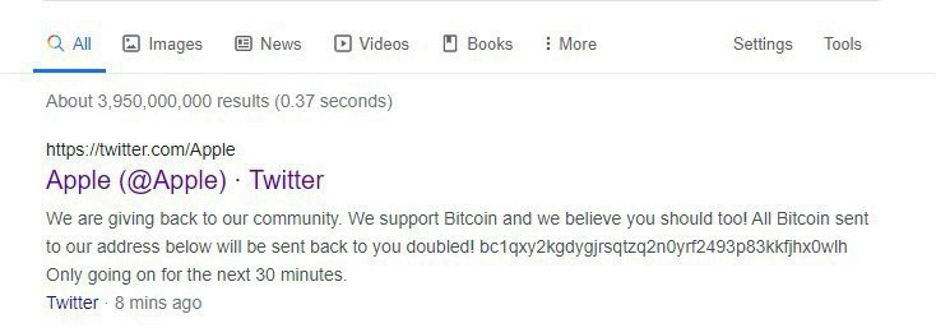
The attackers gained access to several high-profile accounts and tweeted about a cryptocurrency giveaway on their behalf. The messages posted by the attackers promised to double any payments made to a BTC address.
“According to our estimates, during the two hours of the attack, at least 367 users transferred around 120,000 dollars in total to attackers,” said Kaspersky security researcher Dmitry Galov.
Group-IB’s threat researchers were able to identify two cryptocurrency wallets – bc1qxy2kgdygjrsqtzq2n0yrf2493p83kkfjhx0wlh and bc1qwr30ddc04zqp878c0evdrqfx564mmf0dy2w39l – posted by the attackers, and establish that in just hours they had collected more than 13.4 BTC (more than US$121,000).
The total number of transactions associated with these two wallets was 416 at last count. The first transaction was registered at 3:03am Singapore time on 16 July 2020.
Key lessons learnt
David Higgins, technical director at CyberArk, said: “After initially looking like successful social engineering of some key insiders enabled this external hack, there is some talk that more ‘traditional’ methods were used to buy inside cooperation and access to the admin tool that allowed takeover of high profile accounts. Either way, it shows that hackers will always target the privileged access and rights of insiders. In some cases this is through identity takeover but it’s possible that in this case we see an example of the malicious insider at work.”
The clear lesson in this case, he said, is the importance of placing strong controls and monitoring of users that have privileged access to key systems and services. “It’s a clear reminder of why social media – which has emerged as a critical communications conduit – should be treated by companies as critical infrastructure and secured as such.”
Serkan Cetin, APJ technical director at One Identity, concurred that cybersecurity practices used to protect and manage accounts that grant access to sensitive corporate data and enterprise systems should also be utilized for securing access to social media accounts and corporate profiles on social platforms.
“This news demonstrates the importance of privileged access management across all systems, accounts, and applications, even those that many would not traditionally consider critical enough to protect, especially for those which are in the public spotlight,” said Cetin. “This situation exemplifies why it is necessary to implement stronger practices for managing both individual and corporate accounts across social platforms.”
According to Group-IB CEO Ilya Sachkov, the attackers have chosen the most straightforward way possible to capitalize on the level of access they’d gained. “This could have ended far worse, affecting the stock market heavily or even resulting in a geopolitical catastrophe. This is the least they could have done with the God-mode access they had.”
The attack has demonstrated once again the problem of low financial literacy and bad cyber hygiene. “There ain’t no such thing as a free lunch, it’s as simple as that. Anyone who promises you to double your payment and asks for an advance fee is a scammer. Think twice before you transfer your money or confidential personal data,” said Sachkov.
“Hacking into popular accounts to publish scam messages isn’t a new practice, neither is the ‘doubling the donation’ scam,” commented Kaspersky’s Galov. “What is curious in this case is the scale of the attack and the fact that the actor completely took over the verified accounts – their emails have been changed, so the owners aren’t able to get access back quickly enough.”
He added that the scam was extremely effective: “The amount gathered from the victims now equals over US$120,000, and this is just in one day. I think there are two major takeaways from this incident. First, users need to be aware of scams and stay cautious on social media; they need to be able to recognize them. Second, we need to be extra careful with our online assets – anything critical has to have, at a minimum, two-factor authentication.”
This Twitter scam highlights the fact that we are living in an era when even people with computer skills might be lured into scammers’ traps, and even the most secure accounts can be hacked.
“Cybersecurity is undoubtedly one of the top priorities of all major social media platforms,” said Dmitry Bestuzhev, cybersecurity expert at Kaspersky. “However, neither websites nor software are entirely immune to bugs, nor is the human factor immune to mistakes.” As a result, any native platform can be compromised.
“Today we see how, along with new attack vectors, scams combine old and effective techniques, use a surprise element, and gain people’s trust to facilitate the attack and lure victims into a trap.”
For instance, it could be a combination of supply chain attacks with social engineering for the threat actors to gain access to victim’s account in other ways. Or they might penetrate a third-party app with access to the users’ profiles, or users’ passwords might be brute-forced.
What to do
As a precaution, Group-IB advises users to remain extra vigilant and be skeptical of any claims to double payments to a Bitcoin wallet even if they come from official verified accounts.
“However,” said Bestuzhev from Kaspersky, “we urge everyone not to panic and simply accept a new mindset; social media account users require a responsible approach and thorough protection, but we are not lambs to the slaughter.”
“This incident might mean we all need to take some time to reassess our approach to our relationships with social media and accounts’ security, but once we do so, it will become evident that we possess knowledge and instruments to recognize even the most elaborate scam and minimize its impact.”
To recognize scams in social media, Kaspersky advises users to keep in mind:
- The most important element of every scam is a time limit. Not only does it prevent a victim from conducting a thorough check on the matter, but it also adds some psychological pressure on the user, making it easier for them to overlook details. Being afraid of missing a great opportunity, even the most careful people might be seduced into taking a risk and falling for the attackers’ trick.
- In this case, the scam has also been thoroughly tailored to the personality of the owner or the tone of voice of the hacked account, which made it seem legitimate. Criminals might even go further and illustrate the scam with an authentic-looking design or use deepfakes. One must always keep in mind that official campaigns or even individual initiatives of such scale always have prescriptive documents to support even the briefest promo offer, and these are placed outside of social media. In addition, the financial part is usually more transparent and not tied to private bitcoin wallets.
- Remember that it is highly unlikely that any official enterprise or established individual will ask you to transfer money, even to return to them later or as a joke due to possible issues with taxes and financial reporting.
Some tips to maximize the protection of your account in social media:
- While it is absolutely essential to have a strong password, it should also be unique, so that if other website leak your credential, your accounts remain safe. To create safe and complicated passwords for each website, use memory techniques or a password manager.
- Use two-factor authentication—where your login and password need to be confirmed by entering a special code. Furthermore, consider not using a text message to receive this code, as it can be hijacked, but an app that generates such codes. Alternatively, use a physical key, connected to the separate device through USB-cable or NFC.
- Another security measure that needs to be taken is a thorough review of the apps that have access to your Twitter account. They can be found in the Twitter account settings. We recommend revoking access to your account from all of them, or the ones that you don’t consider thoroughly protected, so that, in the event of a hack, your account can’t be reached.
- Start using services such as “Privacy Checker” to help make your social media profiles more private. It will make it harder for third parties to find highly personal information.

















