What are the riskiest connected devices around us today, and how should we address the cyber risks they pose?
According to Forescout’s recent Rough Around the Edges report, there are 22 million exposed OT devices in the ASEAN region alone – 21% more than two years ago. In ASEAN,Singapore has the highest exposed OT devices, with a risk level of 23.89%, followed by Vietnam (21.06%) and Thailand (19.52%). Although the most exposed devices does not necessarily mean the most compromised, the exposure can still be worrying.
Meanwhile, IT devices – such as network infrastructure and endpoints – still account for the most vulnerabilities globally at 58% despite being down from 78% in 2023.
Together, the vast number of exposed IT, IoT, OT and IoMT devices pose a huge risk for organizations and nations regionally and globally.
We discuss the vulnerabilities, threats and blind spots in connected devices around us that pose serious cyber risks today – and how we should deal with them – with Daniel dos Santos, Head of Security Research, Forescout Technologies.
What are some connected devices with the most vulnerabilities and blind spots, posing the most cyber risks to businesses?
Daniel dos Santos (DS): We publish an annual report highlighting the riskiest connected devices across four categories: IT, IoT, OT and IoMT (medical devices). This is the fifth year we publish this report and we noticed that some types of devices have been consistently risky, for instance: IP cameras and VoIP equipment in IoT, programmable logic controllers in OT and medical imaging devices in IoMT.
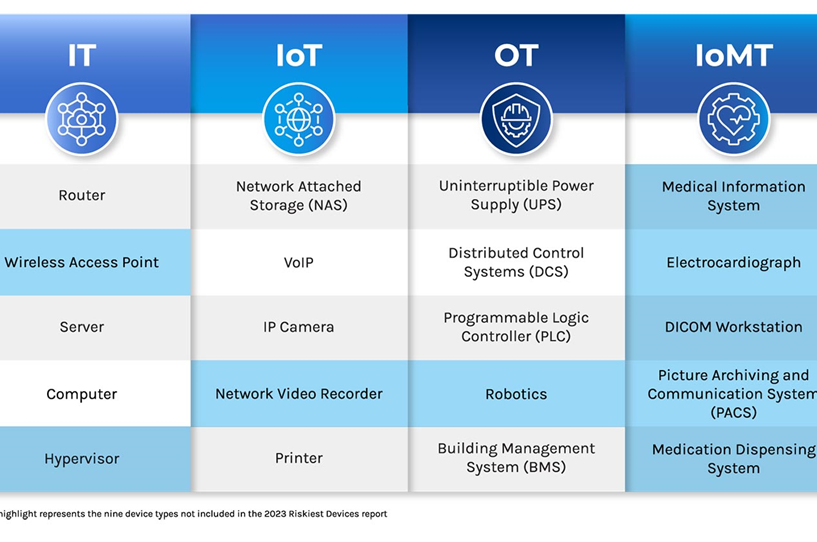
What they have in common is not only that they often have vulnerabilities but also that they are very often misconfigured, exposing dangerous network services that could be disabled or relying on default or weak credentials. On top of that, these devices are unmanaged, in the sense that they do not run the typical security agents you would find on a workstation that allow IT teams to have greater visibility and control on devices.
One type of IT device we saw becoming riskier this year is network infrastructure: routers, wireless access points, switches, VPN appliances and so on. This type of device is nowadays being constantly targeted by threat actors who find new vulnerabilities and exploit them in either very targeted campaigns or massively across a larger number of organizations. They are also very risky because they tend to be at the perimeter of the network, thus allowing for a great level of access if they are breached.
What are some system integrator or internal IT practices that may create blind spots on an organization’s network, leaving devices vulnerable to attacks?
DS: A few examples include:
- Using devices with their default configurations, which may include services that are not needed and weak credentials.
- Granting too broad access to suppliers, integrators and other third-parties to perform monitoring, maintenance and configuration remotely.
- Failing to maintain an automatically updated asset inventory, thus creating blind spots on the network.
- Not including cybersecurity requirements in the acceptance tests when new assets are commissioned on the network.
What types of OT devices and protocols are most often exposed on the Internet? How are hacktivists targeting these devices?
DS: Currently, devices such as programmable logic controllers (PLCs) running the Modbus protocol represent around a third of exposed OT devices. These devices are used to directly monitor and control industrial processes such as manufacturing, water treatment and many others. The fact that they expose a protocol that lacks authentication and can be used to directly change their parameters is very worrying.
Another third of exposed devices are those running building automation protocols such as KNX, BACnet and Fox. These devices control important functions in smart buildings such as physical access control, heating, ventilation and air conditioning. The remaining third includes a myriad of other devices and protocols such as S7, EtherNet/IP and IEC-104.
Hacktivists usually target these devices as part of opportunistic campaigns where they define a broad set of targets (e.g. companies in a certain country), use tools that scan the Internet (such as Shodan, Censys and FOFA) to find exposed devices in those targets and do one of the following:
- Directly use exposed weak protocols such as Modbus to tamper with their parameters, hoping to cause a physical disruption.
- Manage to get access to their graphical interface – human-machine interfaces – and deface them or also tamper with settings.
- Cause denials of service to bring these devices offline.
How can organizations reduce risk exposure from such devices and protocols?
DS: There are three main risk mitigation measures that we recommend to organizations:
- Harden connected devices by maintaining an accurate asset inventory, disabling unused services, patching known vulnerabilities and using strong credentials.
- Do not expose unmanaged devices directly to the internet, with very few exceptions such as routers and firewalls. Ensure threat the administrative interfaces in those devices are segmented behind access control lists and VLANs.
- Monitor the network for signs of intrusion to alert on known or suspicious malicious behaviour.