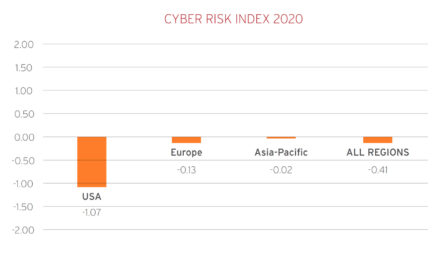
Will the delayed and nonchalant disclosure of the hacks in 2019 be a lesson learnt or an invitation for worse attacks?
On 30 August 2019, officials at the UN’s Geneva branch issued an alert about a hacking incident. That was more than a month after the initial detection.
According to reports, the incident was a major breach that had been kept under wraps. UN spokesperson Stéphane Dujarric, who had classified it as ‘serious’, had been quoted as saying: “As the exact nature and scope of the incident could not be determined, [the UN offices in Geneva and Vienna] decided not to publicly disclose the breach.”
The breach affected at least 42 of the organization’s core servers in Vienna, Geneva and the UN Office of the Higher Commissioner for Human Rights (OHCHR) HQ in Geneva. Lists of user accounts “would have been exposed”, while other vague disclosures cited 10 other “infrastructure components” such as printing, antivirus and human resource management systems, had been compromised.
According to a Forbes report, the hackers used a known vulnerability (CVE-2019-0604) in an internet-facing Microsoft SharePoint server, a web-based collaborative platform integrated with Microsoft Office. Although Microsoft had issued fixes for this way back in March 2019, the UN administration had not patched their servers. Subsequent forensics uncovered the fingerprints of an Advanced Persistent Threat actor. This means the attack was most likely a “well-resourced” campaign by a nation state.
Critics have slammed the UN, whose role is to govern nation-state behavior, had not been transparent and vigilant about the serious breach. In response, the UN had downplayed the fallout of the breach: “Although hackers accessed a self-contained part of our system in July 2019, the development servers they accessed did not hold any sensitive data or confidential information. The hackers did manage to access our Active User Directory, which contains the user IDs for our staff and devices. However, they did not succeed in accessing passwords. Nor did they gain access to other parts of the system. Once we became aware of the attack, we took action to shut down the affected development servers.”
According to Shay Nahari, Head of Red Team Services, CyberArk: “The compromise of core infrastructures at the UN is troubling— especially considering the specific offices targeted and the information they hold. One of the most critical steps for the UN to take now should be focused on strategic post-breach actions focused on remediation—such as ensuring credentials are properly managed, rotated and audited to stop additional incidents or any attempt at lateral movement. Once attackers gain control over an entire infrastructure, they can persist and hide to have a longer-term presence. How they got in, or why, is irrelevant now.”