In 2024, developers across GitHub used secret scanning to detect more than 39 million secret leaks, according to GitHub’s Octoverse 2024 report.
The last year (October 2023 to September 2024) saw developers and open-source communities responding more quickly to security incidents through new generative AI security tools, automated alerts, and proactive measures. This isn’t just helping make software more secure — it’s leading to faster fixes, too.
While GitHub is raising the bar for security and building tools that integrate seamlessly into developers’ workflows, developers are not security experts, “and that’s why we’re going to continue to see more and more adoption of automated security tools to help close that cybersecurity gap – both within the open source community and in private use – with tools such as secret scanning and code scanning that are going to help clean up and eradicate vulnerabilities at scale,” said the company’s CISO Alexis Wales.
The most common security vulnerabilities

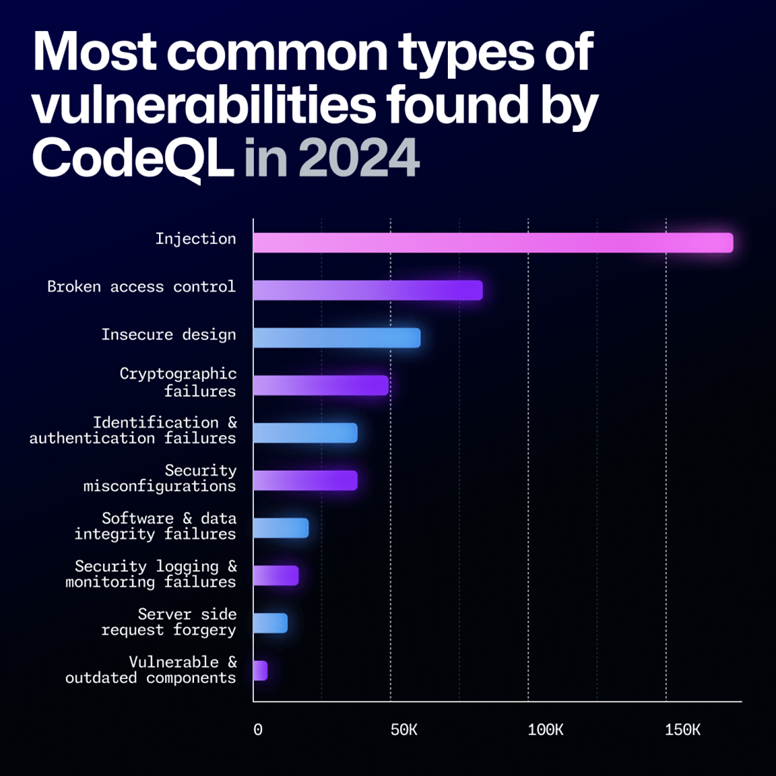
Injection, an admittedly large category of security issues, was the most common type of vulnerability found across public and private repositories via CodeQL, a code analysis engine developed by GitHub to automate security checks. Meanwhile, Security Logging and Monitoring Failure vulnerabilities were found more often in private repositories.
Increased use of AI for code reviews and security vulnerability remediation
AI doesn’t replace security experts, but it can augment their knowledge and capabilities while helping address a global shortage of security professionals.
Notably, developers are experimenting with AI tools like Copilot Autofix, an AI-powered security tool that automatically detects vulnerabilities and suggests fixes while offering explanations in natural language.
GitHub expects tools like this to improve security across open source and public projects — as well as with closed source, too. So far, Copilot Autofix has helped developers:
- Fix code vulnerabilities more than three times faster than those who did so manually, reducing time to fix for a pull request-time alert from 1.5 hours to 28 minutes
- Fix cross-site scripting vulnerabilities seven times faster, reducing time to fix to 22 minutes, compared to almost three hours
- Fix SQL injection vulnerabilities twelve times faster, cutting time to fix to just 18 minutes, compared to 3.7 hours
Developers on GitHub are using automation to manage the growing volume of security responsibilities. For instance, developers are merging an increasing number of pull requests generated by Dependabot, which sends alerts about outdated or vulnerable dependencies in a pull request. The gap between pull requests opened by Dependabot and pull requests merged by developers continues to shrink year over year.
Developers automate more aspects of build, test, and security activities
2024 saw developers use 10.54 billion total GitHub Actions minutes (measured in CPU minutes). That’s up almost 30% year over year from the 7.3 billion GitHub Actions minutes developers used in 2023.
The rising number of developers employing automation was mirrored by growth in the number of GitHub Actions in the GitHub Marketplace. Some of the most popular actions include Gosec Security Checker, Super-Linter, PHPLint, and Metrics embed.
“We get everything we need from the GitHub Actions marketplace to build and support our tailored CI/CD pipeline,” said Bjoern Bengelsdorf, Senior Software Engineer, Otto Group.
Among the most popular GitHub Actions in the GitHub Marketplace are OpenCommit, which augments commit messages with meaningful AI-generated content when pushing to remote, and Replexica, which provides AI-powered code translations across multiple programming languages.
These actions suggest that developers are finding more use cases for generative AI in their workflows.
The CISO’s role in DevOps
A challenge for the CISO population, however, is how to have clear communications with business leaders, to provide an effective and clear understanding of what risks may or may not emerge from the use of AI within an enterprise, said Wales.
“Oftentimes, when things are confused or translation is not clear, it can create a fear-based culture, which is not ideal for decision making. So one of the things I appreciate about GitHub is that we have a really wonderful storytelling approach that is not based in heavy technical jargon or language, and we really are working on bringing awareness and benefits of our product lines to the DevOps realm in a very non-technical way, so that business users and company leadership can understand what they need to be concerned about or what they don’t need to be concerned about.”
Yet more needs to be done
While developers are using automation and AI to secure their code and applications, there’s room for improvement.
Government regulations increasingly demand developers know the ingredients going into their software artifacts, which increases demand for implementing tools that automate governance and compliance.
Becoming familiar with GitHub security features, such as code scanning and secret scanning (which are free for open source developers), and supply chain governance features like artifact attestations is a good first step towards automating best security practices.
Wales said: “There’s more we can do in creating greater threat awareness throughout the developer lifecycle, and for this awareness to be infused in all of the developer tooling that we have. There’s always room for some improvement, but I think we’re on the right track in the way we have been building out our advanced security offerings.”
Regulating the global software supply chain
According to Wales, GitHub is actively working to harmonize global regulations and build trust in AI-powered software development through several key initiatives:
- Public-private partnerships: GitHub is engaging directly with policy makers around the world to have early and upfront conversations about the impact of AI and the needs of the developer community. This helps ensure regulations are informed and current.
- Transparency and education: GitHub is focused on providing transparency around its responsible AI practices and policies, as part of Microsoft. This includes publicly sharing its standards and making efforts to educate both policy makers and the public on the value and importance of open source and AI-powered development tools.
- Secure software supply chain: GitHub is investing heavily in advanced security features like code scanning, secret scanning, and dependency awareness. The goal is to maintain a secure software ecosystem and proactively address vulnerabilities at scale.
- Seamless security integration: GitHub recognizes that developers are not security experts, so it is working to build security tools that integrate seamlessly into developers’ workflows. This helps reduce the security burden on individual developers.
- Building trust through community By fostering a strong, global developer community, GitHub aims to amplify the voice of developers and ensure their needs and concerns are represented in policy discussions. This helps build trust between the industry, policy makers, and the public.
The key is to focus on open communication, transparency, and collaborative partnerships to harmonize regulations and build trust in AI-powered software development. This multi-faceted approach is critical as the software industry and governments work to responsibly harness the power of transformative technologies.

















