By weaponizing two established protocols to phish for the trust of their unsuspecting targets, scammers have successfully wiped out crypto wallets
In the world of crypto transactions protected by Blockchain ledger technology, fraudsters have finally found ways to circumvent the safeguards to conduct their scams, according to Check Point Research (CPR).
To manipulate potential victims into approving transactions, attackers often use social engineering techniques by sending phishing emails or messages that appear to be from trusted sources.
Now, to evade detection and increase the apparent legitimacy of their phishing, cybercriminals are weaponizing recognized addresses from Uniswap and Safe, to disguise their malicious activities. How?
The modus operandi
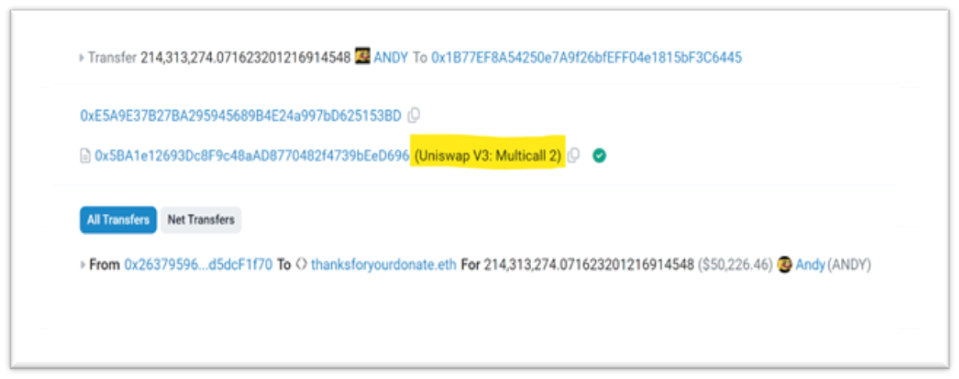
Fraudsters can embed their attacks within the multicall aggregate function on a Uniswap V3 contract, which allows them to execute multiple transactions in a single call, thereby obfuscating their true intentions.
Similarly, they can utilize the GnosisSafeProxy contract to create seemingly legitimate contracts, which are then used to perpetrate fraudulent schemes.
If potential victims check the multicall contract address on platforms like Etherscan, and see that it is labeled as associated with Uniswap, they could mistakenly assume it is safe. This perceived safety can be dangerous as a decentralized exchange (DEX) regularly interacts with user wallets for transactions.
Attackers can leverage the multicall contract to orchestrate fund transfers from victims’ wallets to their own. They do this by using Uniswap as the spender address: unsuspecting users, seeing Uniswap listed as the spender and trusting its legitimacy, may then approve transactions they believe are standard operations. This approval unwittingly grants permission for the transfer of their assets directly into the attackers’ wallets.
Also, in a scam detected by CPR earlier this year, cybercriminals coaxed unsuspecting victims into signing off on fraudulent transactions on the Safe (formerly known as Gnosis Safe) infrastructure. Initially, the attackers establish a legitimate proxy contract. Next, they trick the targets into engaging with this proxy contract, persuading them to carry out an “increase allowance” transaction. This action then authorizes the attackers to manage tokens from the victims’ wallets.
Crypto safety advisory
This abuse of trusted protocols not only enhances the credibility of their scams but also makes detection and prevention significantly more challenging.
In light of this developing vulnerability CPR recommends crypto investors to avoid blindly accepting transactions, even if they appear to come from trusted sources.
Whenever possible, perform actions directly from the official project websites to ensure authenticity. Also, it is prudent to regularly monitor crypto wallet and transaction histories for any unusual activity.
Finally, crypto users need to stay updated on the latest scams and risks through active monitoring of blockchain cybersecurity news and community concerns.
According to CPR’s Chief Technologist & Head of Products Vulnerability Research, Oded Vanunu: “This new vulnerability underscores the increasing sophistication of cybercriminals targeting the crypto space, revealing not just the need for user vigilance, but the urgent necessity for advanced security measures and continuous education. As decentralized finance platforms continue to grow… such breaches can result in long-term damage to user trust and the broader adoption of decentralized technologies.”