Thousands of years after this astute observation, cyber warfare continues the tradition in more ways than Sun Tzu could have imagined…
According to a cyber-threat report by Microsoft, on 23 February 2022, , we entered a new age of hybrid war, where hours before missiles were launched and tanks rolled across borders, Russian actors had already launched a massive destructive cyber-attack against Ukraine’s government, technology, and financial sector targets.
On a broader scale, this trend has implications across the entire cybersecurity landscape, which can be categorized into five areas: general cyber-landscape trends, state-sponsored threats; devices and infrastructure; cyber resilience, cyber influence ops.
Following are some notable takeaways from the report, created from the technology giant’s massive ecosystem of researchers and corporate partners during the period 1 July 2021 through 30 June 2022:
- General state of the cybersecurity landscape
- Human-operated ransomware was the most prevalent cybersecurity threat, as one-third of targets were successfully compromised by criminals using these attacks, including 5% of ransom victims.
- Industrialization of the cybercrime economy had lowered the skill barrier to entry by providing greater access to tools and infrastructure. Presumably, this had led to ransomware and extortion threats becoming more audacious during the period of study, with attackers targeting governments, businesses, and critical infrastructure.
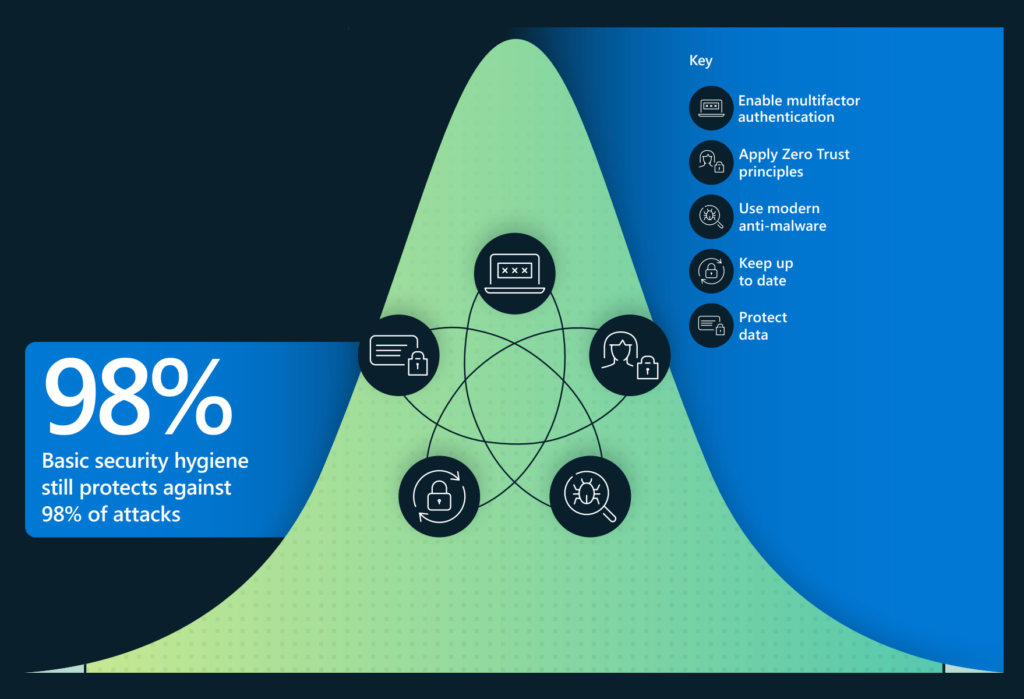
- Multifactor authentication, quick and timely application of tested security patches, and Zero Trust principles, were identified as the most effective defense against ransomware.
- A rise in hacktivism has been observed, comprising disruptions caused by private citizens conducting cyber-attacks to further social or political goals. Thousands of individuals around the world, both experts and novices, have mobilized since February 2022 to launch attacks such as disabling websites and leaking stolen data as part of the Russia-Ukraine war.
- It is too soon to predict whether this trend will continue after the end of active hostilities.
- State-sponsored threats
- Supply chains were a key gateway for cybercriminals to gain access to their main target(s). Exploitation of unpatched system vulnerabilities is another key offensive.
- Critical infrastructure particularly in the IT, financial services, transportation systems and communications sectors were increasingly being targeted.
- China, Iran, North Korea and Russia were the prominent players identified in the report as funding or operating state-sponsored advanced persistent threats.
- There is a growing industry of private firms (call them cyber mercenaries or private sector offensive actors) that develop and sell tools, techniques, and services that enable their clients — often governments — to break into targeted installations. These entities often endanger dissidents, human rights defenders, journalists, civil society advocates, and other private citizens.
- Devices and infrastructure
- Malware-as-a-Service had moved into large scale operations against exposed IoT and Operational Technology in infrastructures, public utilities and corporate networks.
- Also notable: leveraging vulnerabilities in IoT device firmware. 32% of firmware images analyzed had at least 10 known critical vulnerabilities
- Attacks on remote management devices had increased five- fold in 2021.
- Governments worldwide were moving to protect critical infrastructure by improving IoT and OT security
- Cyber influence ops
- These activities were becoming increasingly sophisticated as more governments and nation states were using such ops to shape opinion, discredit adversaries, and promote discord.
- Russia, Iran, and China employed propaganda and influence campaigns throughout the COVID-19 pandemic, often as a strategic device to achieve broader political objectives.
- Russia’s invasion of Ukraine demonstrates cyber influence ops integrated with more traditional cyberattacks and kinetic military operations to maximize impact.
- ‘Synthetic media’ is becoming more prevalent: the proliferation of tools that facilitate easy creation and dissemination of highly realistic fake images, videos, and audio has led to this trend. Digital provenance technology that certifies media asset origin holds promise to combat misuse.
- To add to the challenge, private sector technology entities may unwittingly enable cyber influence campaigns. Enablers can include companies that register internet domains, host websites, promote material on social media and search sites, channel traffic, and help pay for these exercises through digital advertising. Organizations must be aware of the tools and methods employed by authoritarian regimes for cyber influence operations so they can detect and then prevent the spread of campaigns.
- There is a growing need to help consumers develop a more sophisticated ability to identify foreign influence operations and limit engagement with cyber influential narratives or content.
- Cyber resilience
- The soundness of an infrastructure’s basic security posture determines how effective advanced solutions will be.
- During the period of study, DDoS activity was unprecedented in volume, complexity and frequency.
- The vast majority of successful cyberattacks in the period of study were deemed to be preventable if basic security hygiene practices had been in place or properly practiced.
- Password-based attacks remained the main source of identity compromise. Strong authentication is needed, involving multiple authentication factors.
Uncannily, all the latest cyber trends and tactics — however rudimentary or sophisticated — still directly or indirectly revolve around the art of deception.
The report has noted how more than three-quarters of people surveyed worried about how information is being weaponized, whether inadvertently, semi-intentionally or maliciously, for “good” intentions or bad.

















