While phishing incidents were definitely increasing in 2023, one cybersecurity firm is suggesting that insufficiently-trained employees was one common denominator
In analyzing its protection ecosystem metrics for 2023, one cybersecurity agency has announced “financial-phishing” trends encountered among its customers in South-east Asia (SEA).
Financial-phishing refers to phishing incidents related to banking, payment systems and digital retail transactions where users of business devices are involved.
Those in the Philippines logged the highest number of financial phishing incidents at 163,279 attempts, followed by Malaysia with 124,105. Indonesia customers chalked up 97,465 incidents while those in Vietnam experienced 36,130 phishing attacks related to financial matters. Thailand and Singapore customers 25,227 and 9,502 financial-phishing attempts respectively.
In total, the metrics showed nearly 455,700 attempts (from Jan to Dec 2023) to follow a phishing link related to finance matters on business devices in South-east Asia (SEA) customers of various sizes.
The statistics from Kaspersky reflect user clicks on phishing links placed in various communication channels, including emails, fraudulent web sites, messengers, social media, etc. According to the firm’s general manager for SEA, Yeo Siang Tiong: “Phishing is a technique trusted by cybercriminals when it comes to infiltrating business networks. The rise of generative AI helps cybercriminals to make phishing messages or scam resources more convincing. As a result, it becomes challenging for people to distinguish between a scam and a legitimate communication.”
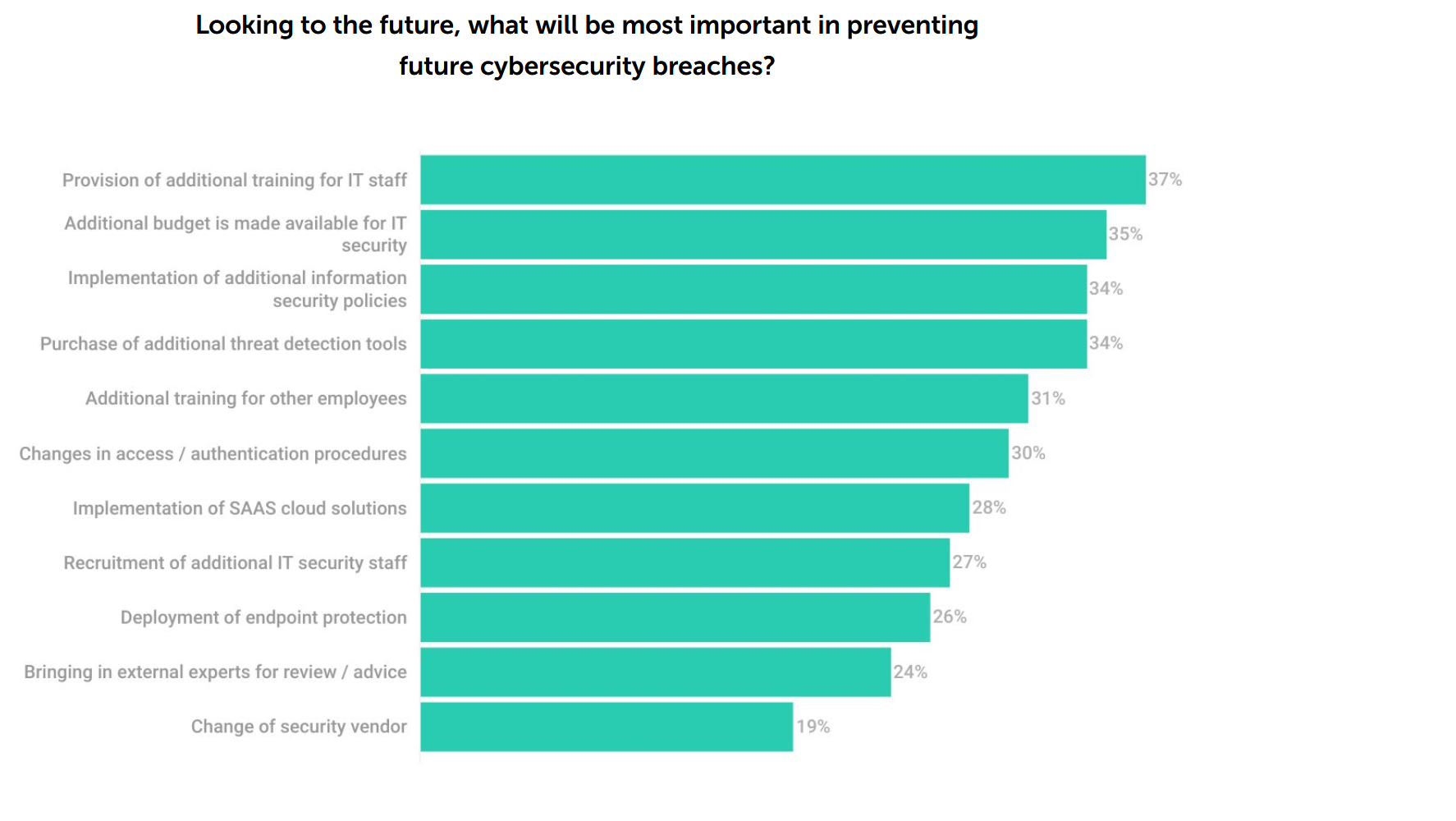
The firm has asserted that employee security violations in the region can be as damaging as external hacking incidents. Citing the “human factor” as part of the most common causes of “accidental” security violations and cyber incidents, the firm believes the current shortage/leanness of IT and cybersecurity staff numbers renders human-factor risks even more concerning.
Yeo said the human factor continues to play a role in making businesses vulnerable. Therefore, in addition to investing in anti-phishing software, endpoint detection and response and other best cybersecurity best practices, organizations need to continually educate employees on cyber awareness, upskill IT personnel to keep ahead of threats, and maintain continual vigilance.