Stolen COVID-19 test results can earn cybercrooks a pretty penny, and even inexperienced hackers can get in on the action.
Today, if you ran out of groceries, just a few taps on your smartphone app and the eggs and bread can be delivered to you in a few hours.
Need some ransomware to target people who have tested positive for COVID-19? Just do into the Dark Web and buy Ransomware-as-a-Service (RaaS)! Yes, that is exactly how convenient it is to commit cybercrime nowadays, especially with the pandemic raging globally. One cybersecurity solutions firm recently did a review of its 2020 client data and found that COVID-19 test results have been growing into a hot community in the cyber-underworld. Here are their findings:
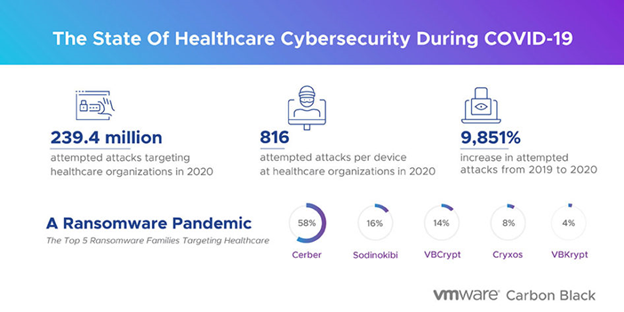
- There were 239.4 million attempted cyberattacks targeting VMware Carbon Black healthcare customers.
- The surge in healthcare sector attacks began around February 2020 just as the pandemic was declared: there was an average of 816 attempted attacks per endpoint in 2020, a 9,851% increase from 2019.
- From January to February 2020, the number of attempted attacks had shot up by 51% as cybercriminals set their sights on vulnerable healthcare organizations that were navigating tremendous changes in operational and treatment policies.
- In H2 2020, attempted attacks per endpoint peaked with an 87% increase from September to October.
- Protected health information (PHI) is being bought and sold on Dark Web markets as an easy way for hackers to cash in on data. Cybercriminal tactics are now being leveraged to facilitate long-term cyberattack campaigns, happening across the digital healthcare supply chain and leading to a surge of ransomware extortions (and double-extortions).
The firm’s spokesman, senior cybersecurity strategist Greg Foss, commented: “COVID-19 test results are a hot commodity on the dark web right now, mostly in the form of large data dumps. Even underqualified, lesser-known cybercriminal groups are behind them thanks to the rise in RaaS. All it takes is a quick search on the dark web for someone to license out a ransomware payload to infect targets.”

















