Automation and XaaS services need not be limited to innocent goals: now, they even leverage legitimate resources to remain elusive.
A global threat hunting and cyber intelligence company has analyzed the tools used to create phishing web pages (phishing kits) and confirmed that, in the past year, such tools have most often been used to generate web pages mimicking online services, email clients, and financial organizations.
Increasingly, cybercriminals use legitimate services such as Google Forms and Telegram to obtain user data stolen on phishing websites. In addition, the Dark Net is marketing ready-to-go platforms that automate phishing using Telegram bots at their core. Such turnkey solutions are distributed under the Cybercrime-as-a-Service model, which subsequently leads to more groups conducting attacks and widen the scope of cybercriminal activity.
A phishin’ we will go
According to the computer emergency response team (CERT) of Group-IB, the firm that announced the findings, in 2019 and 2020 the main target of cybercriminals were online services (30.7%). By stealing user account credentials, hackers gained access to the data of linked bank cards in those services. For 2020, email services became less appealing to cybercriminals, as the share of phishing kits targeting them had dropped to 22.8%. Coming in at third place were financial institutions, with their share totaling above 20%.
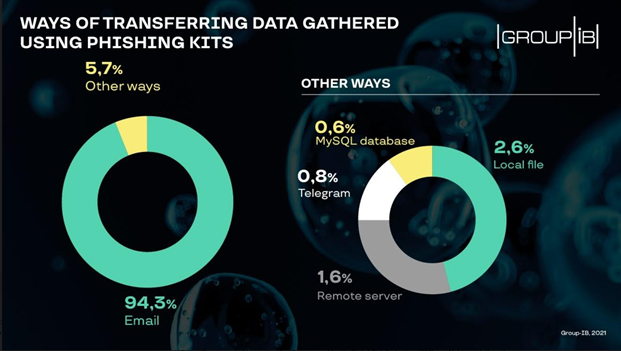
To deceive users into submitting sensitive data, cybercriminals mainly resort to free email services to which all the info harvested on phishing websites is automatically sent. Free emails make up 66% of the total number of emails found in phishing kits. Most email accounts detected were created using Gmail and Yandex.
The functionality of phishing kits is not limited to generating fake web pages to steal user data. Some upload malicious files to the victim’s device. Sellers of phishing kits sometimes even cheat their own buyers, attempting to make money off them twice. How? Apart from selling the malicious tool they created, they may also have their eyes on the data stolen with its help. By using a special script embedded in the text body of the phishing kit, they direct the stream of stolen user data to their own network hosts or intercept access to their customers’ hosting service.
Leveraging automation for cybercrime
Said Yaroslav Kargalev, the deputy head of Group-IB’s CERT: “In the fight against cybercrime, phishing kits have changed the rules of the game. In the past, cybercriminals stopped their campaigns and switched to other brands after the fraudulent resources had been blocked. Today, they automate their attacks and instantly replace the blocked phishing websites with new web pages. In turn, automating such attacks leads to the spread of more complex social engineering used in large-scale attacks rather than separate incidents. This keeps one of the oldest cybercriminal professions afloat.”
In light of this growing trend, organizations should not just block phishing pages but identify and block all the elements of the attackers’ infrastructure and block the entire network of fraudulent resources rather than separate phishing pages, the firm said.