A stern warning to users of the largest marketplace for non-fungible tokens: system vulnerabilities in this technology may still be lurking.
In the past few weeks, researchers had been observing spotted various incidents where people were claiming they lost their crypto wallet balance while receiving a free gift on the OpenSea market place, an established digital collectible marketplace.
Since crypto coins are not regulated in many countries around the globe, it leaves consumer wallets as an attractive target for hackers. In the recent incidents, collectors lost hundreds of thousands of dollars’ worth of NFTs after receiving a free gift from a stranger, or a link to OpenSea art.
One victim confirmed interacting with an airdropped NFT object prior to the account theft, according to Check Point Research (CPR) investigators.
How was it done?
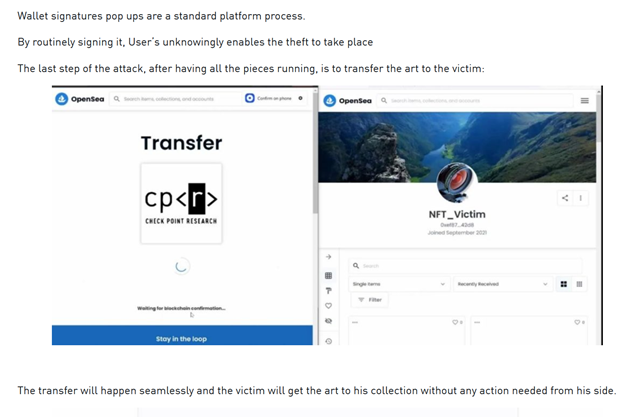
CPR was able to identify critical security flaws in OpenSea, proving that a malicious NFT could be used to hijack accounts and steal crypto wallets. Successful exploitation of the vulnerabilities would have required the following steps:
- Hacker creates and gifts a malicious airdropped NFT to a target victim
- Victim views the malicious NFT, triggering a pop-up from OpenSea’s storage domain, requesting connection to the victim’s cryptocurrency wallet (such pop-ups are common in the platform on various other activities)
- Victim clicks to connect their wallet, in order to perform action on the gifted NFT, thus enabling access to the victim’s wallet
- Hacker can obtain the money in the wallet by triggering an additional pop-up, which is also sent from OpenSea’s storage domain. The user may click on the pop-up, if they do not notice the note in the pop-up describing the transaction
- The end-result could be theft of a user’s entire cryptocurrency wallet
Official statement
Upon responsible disclosure of findings to OpenSea, the issue was fixed and verified. OpenSea also released a statement stating: “These attacks would have relied on users approving malicious activity through a third-party wallet provider by connecting their wallet and providing a signature for the malicious transaction. We have been unable to identify any instances where this vulnerability was exploited but are coordinating directly with third-party wallets that integrate with our platform on how to help users better identify malicious signature requests, as well as other initiatives to help users thwart scams and phishing attacks with greater efficacy. We are also doubling down on community education around security best practices and have kicked off a blog series on how to stay safe on the decentralized web.”
Mitigation advice
NFT collectors are advised to carefully review requests to sign any wallet. If in doubt, reject the request and examine further.
Said CPR’s Head of Products Vulnerabilities Research, Oded Vanunu: “Blockchain innovation is fast-underway and NFTs are here to stay. Given the sheer pace of innovation, there is an inherent challenge in securely integrating software applications and crypto markets. Bad actors know they have an open window right now to take advantage of, with consumer adoption spiking, while security measures in this space still need to catch up. The cybersecurity community must step up to help pioneering blockchain technologies secure crypto assets of consumers.”






![Pssst! [Celebrity name here] wants to share a big crypto tip with you!](https://cybersecasia.net/wp-content/uploads/2022/09/Pssst-Celebrity-name-here-wants-to-share-a-big-crypto-tip-with-you-440x264.jpg)









