Initial Access Brokers : Last year, a rapid cybersecurity response team noticed increased specialization, collaboration and use of ‘as-a-service’ turnkey malware solutions among cybercriminal groups.
A cybersecurity firm’s rapid response team has shared details of various incidents it encountered ‘in the wild’ in 2021.
Summing up, the team’s report shows a 36% increase in dwell time, with a median intruder dwell time of 15 days in 2021 versus 11 days in 2020. The report also reveals the impact of ProxyShell vulnerabilities in Microsoft Exchange, which the team believed were leveraged by Initial Access Brokers (IABs) to breach networks and then sell that access to other attackers.
Additional key findings from respondents’ data include:
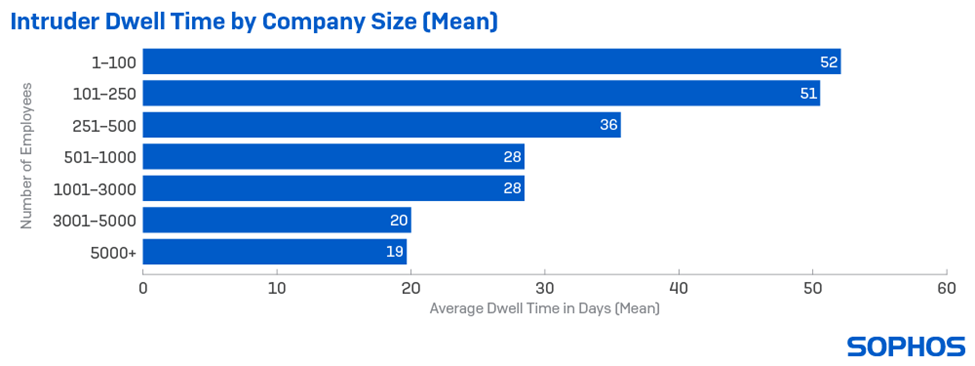
- Among the small organizations in the 2021 rapid response incidents, intruder dwell time was longer. Apparently, attackers lingered for approximately 51 days in corporate clients with up to 250 employees, while spending 20 days in those with 3,000 to 5,000 employees.
- The median dwell time for corporate clients hit by ransomware was 11 days. For those that had been breached, but had not yet been affected by a major attack (such as ransomware, which constituted 23% of all the incidents investigated), the median dwell time was 34 days. Organizations in the education sector or with fewer than 500 employees also had longer dwell times.
- 73% of incidents that the rapid response team responded to in 2021 involved ransomware. Of these, 50% also involved data exfiltration. The mean gap between exfiltration and the issuance of ransom demands was 4.28 days; the median was 1.84 days.
- 18% of incidents handled by the team involved Conti — the most prolific ransomware group seen by the team in 202. REvil ransomware accounted for one in 10 incidents, while other prevalent ransomware families in the firm’s user base included DarkSide, the RaaS behind the notorious attack on Colonial Pipeline in the US, and Black KingDom, one of the ‘new’ ransomware families to appear in March 2021 in the wake of the ProxyLogon vulnerability.
Commenting on this, John Shier, Senior Security Advisor, Sophos, which released the incident report said: “IABs have developed a cottage cybercrime industry by breaching a target, doing exploratory reconnaissance or installing a backdoor, and then selling the turnkey access to ransomware gangs for their own attacks. In this increasingly dynamic, specialty-based cyber threat landscape, it is vital that defenders understand what to look for at every stage of the attack chain, so they can detect and neutralize attacks as fast as possible.”