Terms such as ‘CV’ and ‘employment’ are now being dangled as clickbait to make victims open malicious documents sent via email.
It’s very likely a worldwide phenomenon, but official figures show that one in four Americans have filed for unemployment during the pandemic thus far—the highest the country has had in its history, surpassing even the era of the Great Depression in the 1930s.
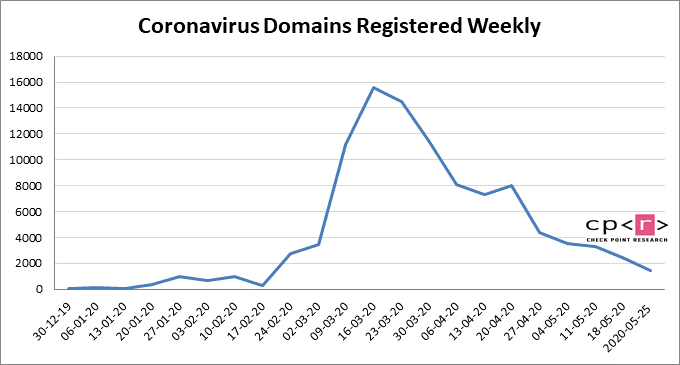
Because of high unemployment rates, people have become more vulnerable to scams and phishing attacks involving government relief package payments. In May 2020, 250 new domains containing the word “employment” were registered. Of these, 7% were malicious and another 9% suspicious. Check Point has reported observing an increase in COVID-themed campaigns in the US, and their ratio, out of all malicious files identified, has doubled in the last two months. One out of every 450 malicious files were found to be a COVID-19 related scam.
Recently, a malicious Zloader malware was used to steal victims’ credentials and other private information. This is a banking Trojan and a variant of the infamous Zeus malware that specifically targets customers of financial institutions.
This is the mechanism of attack: Malicious excel spreadsheets with file names indicating they were individuals’ curriculum vitae (CVs) were sent via email with subjects such as “applying for a job” or “regarding job”. Upon opening the attached file, victims were asked to “enable content” (see image) and when they did, a malicious macro started running, downloading the final payload. Once a device was infected, threat actors could use the malware to carry out financial transactions on the device.
In the United Kingdom and Romania, some companies received an email that looked like this:

The emails came with the subject “CV from China” and contained an ISO file that dropped a malicious EXE file that would run an Info-stealing malware on the user’s machine.
Campaigns that use employment topics as an attack vector are not the only ones taking place. Fake Medical Leave forms were also used to deliver the Icedid malware, a banking Trojan that steals users’ financial data. Malicious documents with names such as “COVID -19 FLMA CENTER.doc“ were sent via emails with subjects like “The following is a new Employee Request Form for leave within the Family and Medical Leave Act (FMLA)”. The emails were sent from different sender domains like “medical-center.space” to lure victims into opening the malicious attachments.
Similarly, another campaign delivered Trickbot, a dominant banking Trojan constantly being updated with new capabilities, features and distribution vectors. In this campaign, the same FMLA theme was adopted, with the emails being sent from domains such as “covid-agency.space”.
Malware attacks increasing after lockdowns
While there was an increase in the number of coronavirus-related attacks, overall, there was a decrease in the total number of cyberattacks, Check Point reported.
In March, when the pandemic was at its peak, their researchers saw a 30% decrease in malware attacks compared to those in January 2020. This was because many countries were going into quarantine and most businesses and other organizations were shut as a result, greatly reducing the potential number of targets for attackers.
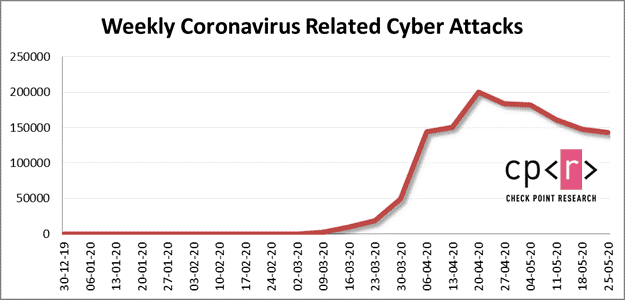
Now with pandemic measures being relaxed or removed, things have started to open up and businesses are running again… and cybercriminals are also ramping up their malicious activities. In May, there was a 16% increase in cyberattacks compared to the period between March and April, when coronavirus was at its peak. This was largely due to an increase in malware attacks.
In May, an average of more than 158,000 coronavirus-related attacks each week. When compared to April, this was a 7% decrease.
As for coronavirus-linked domains, 10,704 new coronavirus-related domains have been registered over the past 4 weeks. Of these, 2.5% were malicious (256) and another 16% (1,744) suspicious.