In some variants, no theft of credentials are needed—just an access token to be granted.
A new type of brand-impersonation attack is using Google-branded phishing sites to trick victims into entering login credentials, according to new research from cloud-security provider Barracuda.
Detecting nearly 100,000 cases of this attack vector in the first four months of 2020, the new form-based attacks make up 4% of all spear phishing attacks studied during the period: a number that researchers expect to climb as cybercriminals see success in harvesting credentials using these attacks.
The form-based attacks are a new kind of ‘brand impersonation’ attack, which sees scammers leveraging the trustability of productivity sites like docs.google.com to convince victims to hand over their credentials.
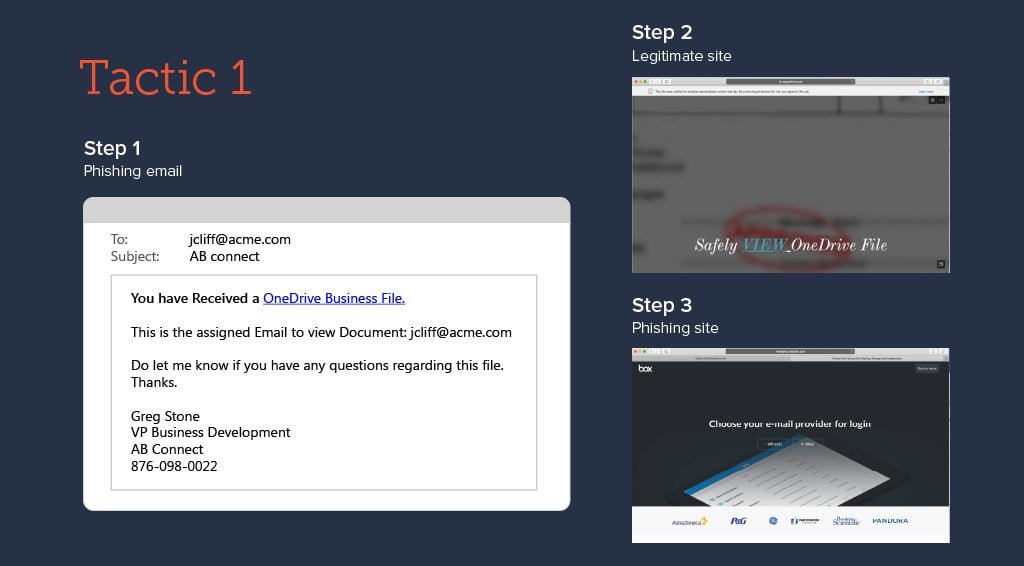
In these attacks, unsuspecting users receive an email that appears to have been generated automatically by file sharing sites like OneDrive, and are taken to a phishing site through a legitimate file sharing site, which makes detection tougher. Attackers also create online forms using legitimate services like forms.office.com, which resemble a login page of a legitimate service, and the link to the form is then included in phishing emails to harvest login details.
Sneaky trick discovered
In one particularly tricky variant of these attacks, hackers can get access to their victims’ accounts without stealing their credentials. This is done by sending phishing emails containing links to what looks like an authentic login page, that contains a request for an access token for an app.
After login credentials are entered, the victim is presented with a list of app permissions to accept. By accepting these permissions, the victim is not giving up passwords to attackers, but rather grants the attacker’s app an access token to use the same login credentials to access the account.
Said James Forbes-May, Vice President, Barracuda, Asia-Pacific: “Attacks like these are likely to go unnoticed by users for a long time, as the user used their credentials on a legitimate website. Even two-factor authentication will do nothing to keep attackers out because their malicious app was approved by the user to access accounts.”
Of the nearly 100,000 form-based attacks Barracuda detected between January 1, 2020, and April 30, 2020, Google file sharing and storage websites were used in 65% of attacks. This includes storage.googleapis.com (25%), docs.google.com (23%), storage.cloud.google.com (13%), and drive.google.com (4%).
In comparison, Microsoft brands were targeted in 13% of attacks: onedrive.live.com (6%), sway.office.com (4%), and forms.office.com (3%). The other sites used in impersonation attacks include sendgrid.net (10%), mailchimp.com (4%), and formcrafts.com (2%). All other sites made up 6% of form-based attacks.
According to Barracuda, cybercriminals continue to adjust their tactics to bypass email gateways and spam filters, so instead of relying solely on looking for malicious links or attachments, it is good to us inbox defence that uses AI to detect and block attacks. This can be complemented with Multi-factor authentication (MFA), such as an authentication code, thumb print, or retinal scan, to stay protected. As with all attacks, as people are the first line of defence, providing regular security-awareness training including phishing simulation to educate users about email attacks—including form based attacks—can help them to recognize and report cyberattacks.