Bad news: Ransomware-as-a-Service democratized even newbie hackers to pillage organizations. Good news: Some tenacious rings were smashed by international agencies.
By the end of 2020, the cybercriminal community, fuelled by the pandemic turbulence, had turned ransomware into the biggest cybercrime money artery.
One threat-hunting cybersecurity firm, Group-IB, has analyzed around 500 or more attacks observed it its own incident response engagements and cyber intelligence activity, to conclude that ransomware attacks grew by more than 150% last year.
Based on this parochial data, it can be said that ransomware attacks on average caused 18 days of downtime for the affected companies working with Group-IB, while the average ransom amount had increased almost twofold (amounting to about US$170,000), with Maze, DoppelPaymer, and RagnarLocker being the greediest groups demanding between US$1 million and US$2 million.
In geographical terms, North America, Europe, Latin America, and the Asia-Pacific region (APAC) were the most commonly attacked regions respectively.
The gold rush of 2020
On a technical level, public-facing remote desktop protocol (RDP) servers in the study were the most common target for many ransomware gangs last year due to the move to remote-working. In 52% of all attacks analyzed by the researchers, publicly accessible RDP servers were used to gain initial access, followed by phishing (29%), and exploitation of public-facing applications (17%).
Big Game Hunting—targeted ransomware attacks against wealthy enterprises—continued to be one of the defining trends in the data. Most of the ransomware attacks that Group-IB analyzed occurred in North America and Europe, where most of the Fortune 500 firms are located, followed by Latin America and APAC respectively.
State-sponsored threat actors such as Lazarus and APT27 started to use ransomware during their operations. The top five most active ransomware families, according to Group-IB’s data, were Maze, Conti, Egregor, DoppelPaymer, and REvil. Not all of them lasted for long for various reasons.
Some gangs operating under the Ransomware-as-a-Service (RaaS) model, such as Egregor and Netwalker, were impacted by the police efforts. Another notorious RaaS collective, Maze, called it quits at the end of 2020. Despite these events, the ransomware business continues unabated, with the RaaS driving this unwelcome growth, which researchers peg to constitute 64% of all ransomware attacks it analyzed in 2020.
Finally, the data review unveiled 15 new public ransomware affiliate programs last year.
Most common TTPs
Going by the group’s own data, the most frequently abused interpreter for launching the initial payload was PowerShell because it is built into every Windows-based system and hence can be abused for evasion. Another theme of 2020 was the active exploitation of Linux, with some threat actors adding corresponding versions to their arsenal.
In the credential access stage, threat actors often used brute forcewithNLBrute and Hydra being the most popular tools, based on Group-IB’s IR engagements. To obtain valid privileges, ransomware operators in 2020 often used credential dumping—retrieving all the passwords from the machine. The attackers’ favorite tools in the study were ProcDump, Mimikatz, and LaZagne.
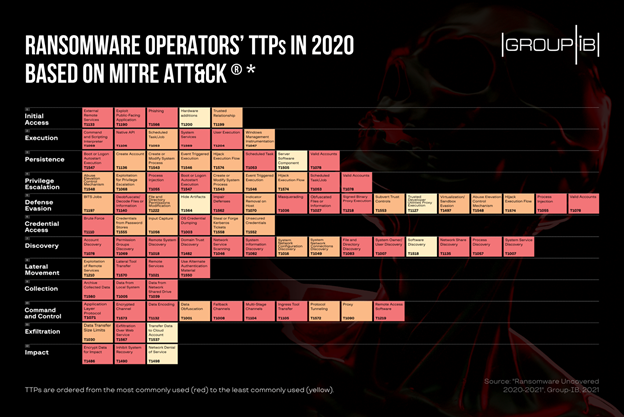
Other findings include a lag time of 13 days on average in the compromised network before the malware started encrypting data. Before deploying ransomware, operators did their best to find and remove any available backups, so that it would be impossible for the victim to recover encrypted files. Another factor that offered cybercriminals a higher success rate, was the exfiltration of critical data to use it as a double-extortion leverage to increase the chances of the ransom being paid. This was the trend set by the infamous Maze collective.
From what used to be a rare practice and an end-user concern, ransomware has evolved last year into an organized multi-billion industry with competition within, market leaders, strategic alliances, and various business models. This successful venture is only going to get bigger from here, according to Oleg Skulkin, Senior Digital Forensics Analyst, Group-IB: “Due to their profitability, the number of RaaS programs will keep growing, more cybercriminals will focus on gaining access to networks for resale purposes. Data exfiltration effectiveness can make it another big niche, with some actors abandoning the use of ransomware at all.”
Skulkin noted that most attacks are human-operated, so it is paramount for organizations to understand how attackers operate, and what tools they use—in order to be able to counter the attacks and hunt for them proactively. “It is everyone’s concern now,” he concluded.