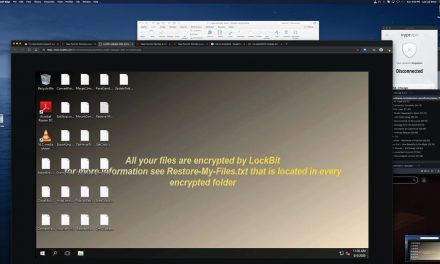
Germany has been badly hit. Ditto for Italy. This is a wake-up call for the region as well.
The toxic Microsoft Exchange Server vulnerabilities have been disclosed and patches released. Organizations that were not protected by holistic cybersecurity solutions have been hit.
Even after the application of official security patches, researchers are witnessing an active growth of attacks attempting to exploit these vulnerabilities, with organizations in Europe and the USA being hit the most.
According to Kaspersky researchers, since the beginning of March 2021, their ecosystem had detected related attacks on over 1,200 corporate users and the number is continually growing. Germany was the worst hit (26.93% of Kaspersky users targeted), with Italy, Austria and Switzerland and the US among the badly hit.
According to Anton Ivanov, VP, Threat Research, Kaspersky: “We had anticipated from the beginning that attempts to exploit these vulnerabilities could increase rapidly, and this is exactly what we are seeing now. So far, we have detected such attacks in essentially in every part of the world. Due to the nature of these vulnerabilities, numerous organizations are at risk.”
Ivanov said that, even though the initial attacks may have been targeted, there is no reason for actors to not try their luck by attacking essentially any organization that runs a vulnerable server. These attacks are associated with a high risk of data theft or even ransomware attacks, and, therefore, organizations need to take protective measures as soon as possible.
The following checklist should have already been followed by due cyber diligence, but it is worth repeating:
- Update Exchange Server with the latest security patches as soon as possible.
- Focus defense strategy on detecting lateral movements and data exfiltration to the internet. Pay special attention to outgoing traffic to detect cybercriminal connections. Back up data regularly. Make sure you can quickly access it in an emergency.
- Endpoint security solutions that incorporate AI-based behavior detection and exploit prevention should do the job of protecting organizations from the continued blind assaults and stop any attempts in the early stages, before the attackers can achieve their goals.
Note that this exploit of a widely-used server system is not the first, and will not be the last. Organizations should take this opportunity to re-evaluate their network security and take perennial measures to remain undaunted by any future vulnerability- and zero-day exploits.