To snare Chinese-language web users, cybercriminals used ads linking to spoofed websites of popular software to spread a remote access trojan
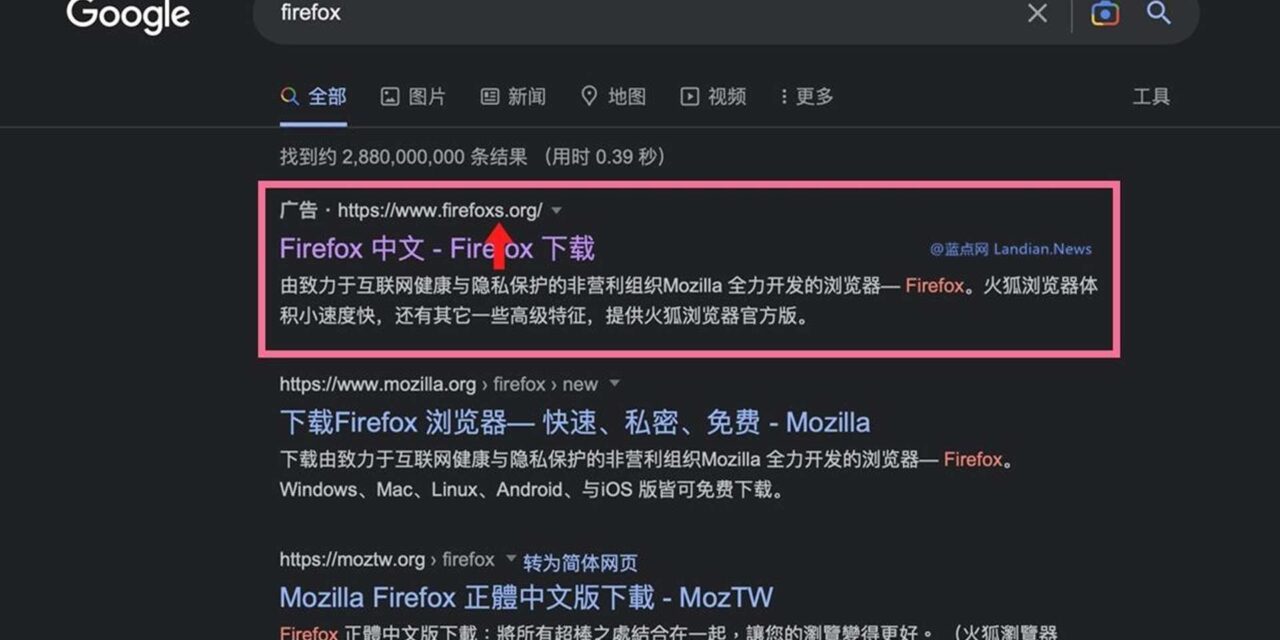
Cybercriminals have been paying to place misleading advertisements to appear in Chinese-language Google search resultsin Taiwan, China and Hong Kong that trick people into thinking they were download popular software from the respective official websites, but which were actually spoofed sites containing trojanized installers.
The unknown attackers first created fake websites that mimic those of popular applications such as Firefox, Line, WhatsApp, Signal, Skype, Telegram, WPS Office, Youdao, Electrum Bitcoin wallet and Sogou Pinyin Method. However, in addition to providing the supposed software, the installers also deliver FatalRAT, a remote access trojan.
The attacks, first spotted by ESET researchers between August 2022 and January 2023, have so far affected users mostly in mainland China, Hong Kong, and Taiwan, but smaller numbers were also spotted in South-east Asia, including Singapore, Indonesia, Japan, Malaysia, Myanmar, the Philippines and Thailand.
Key highlights of the methodology include the cybercriminals’ purchase of advertisements to position their malicious websites in the ‘sponsored’ section of Google search results in Chinese. The spoof websites used ‘typo squatting’ URLs (such as telegraem[.]org or firefoxs.[org]) to throw off potential victims.
The installers downloaded from the resultant spoof websites are mostly in Chinese and, in some cases, falsely offer Chinese-language versions of software that are not available in China. If the potential victims download the fake app, the FatalRAT malware will be activated to provide attackers with a set of functionalities to perform various malicious activities on the victims’ devices.
Depending on specific circumstances, the malware may even conduct checks to determine whether it is running in a virtualized environment. None of the malware or network infrastructure used in this campaign were matched to known activities of any named groups, so the firm has not attributed this campaign to any known group. ESET had reported the incidents, and the malicious ads have been taken down.