The malware has occasionally disappeared for brief spells—but what matters is that organizations should be ready for its eventual return.
In the past weeks, cybersecurity solutions firm Sophos has observed that one of the most prevalent, widely-distributed malware families in the world has reawakened after a prolonged absence.
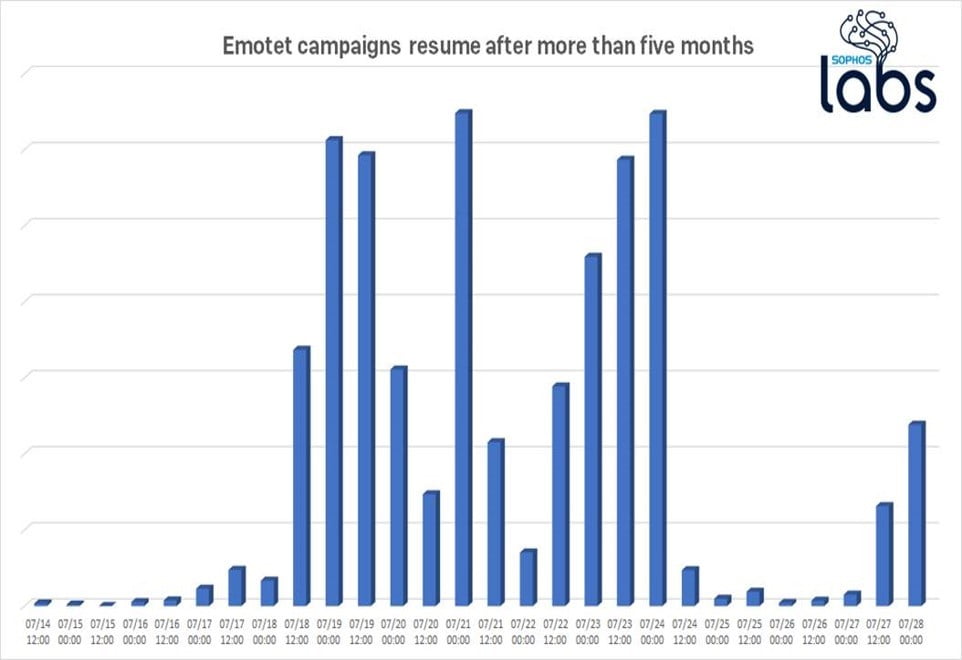
Emotet, the ubiquitous botnet that arrives in the guise of any of a thousand different bogus email messages, never really went away when it suddenly stopped appearing in internal records and feeds of spam emails in February 2020.
The disappearance of the malware left room for assumption that the masterminds behind it had been arrested, had gone into retirement, or perhaps had contracted COVID-19 and were laying low. However, these theories were put to pasture when on 17 July a new wave of Emotet attacks were detected.
Emotet is not merely a tool for thievery—the botnet acts as a delivery mechanism for other malware, walking the code through firewall over the encrypted channels it creates, thereby bypassing network-based defences.
According to Richard Cohen, Senior Threat Researcher, Sophos: “We’ve talked a lot about Emotet in the past, including explaining its malware ecosystem, providing a series of deep-dive 101s, and showing how the malware authors vented their frustration at Sophos by embedding a plaintext note to us in their source code. But, then in February 2020, Emotet ceased production. Its botnets stopped activity and the waves of spam campaigns went silent. This isn’t the first time Emotet has vanished off the radar, only to rise again months later—and that’s exactly what we saw again.”
Cohen said that Emotet’s fundamental method of attack has not changed, and users should be wary of emails from any unknown sources, or even emails from a known source but in an unexpected manner, with a Microsoft Office file attached: be extremely careful about opening such mails.

















